To filter routes in EIGRP protocol I have these options:
1. Filtering with Passive Interface
2. Filtering with Prefix-Lists
3. Filtering with Standard Access-Lists
4. Filtering with Extended Access-Lists
5. Filtering with Offset Lists
6. Filtering with Administrative Distance
7. Filtering with Per Neighbor AD
8. Filtering with Route Maps
9. Per Neighbor Prefix Limit
10. Redistribution Prefix Limit
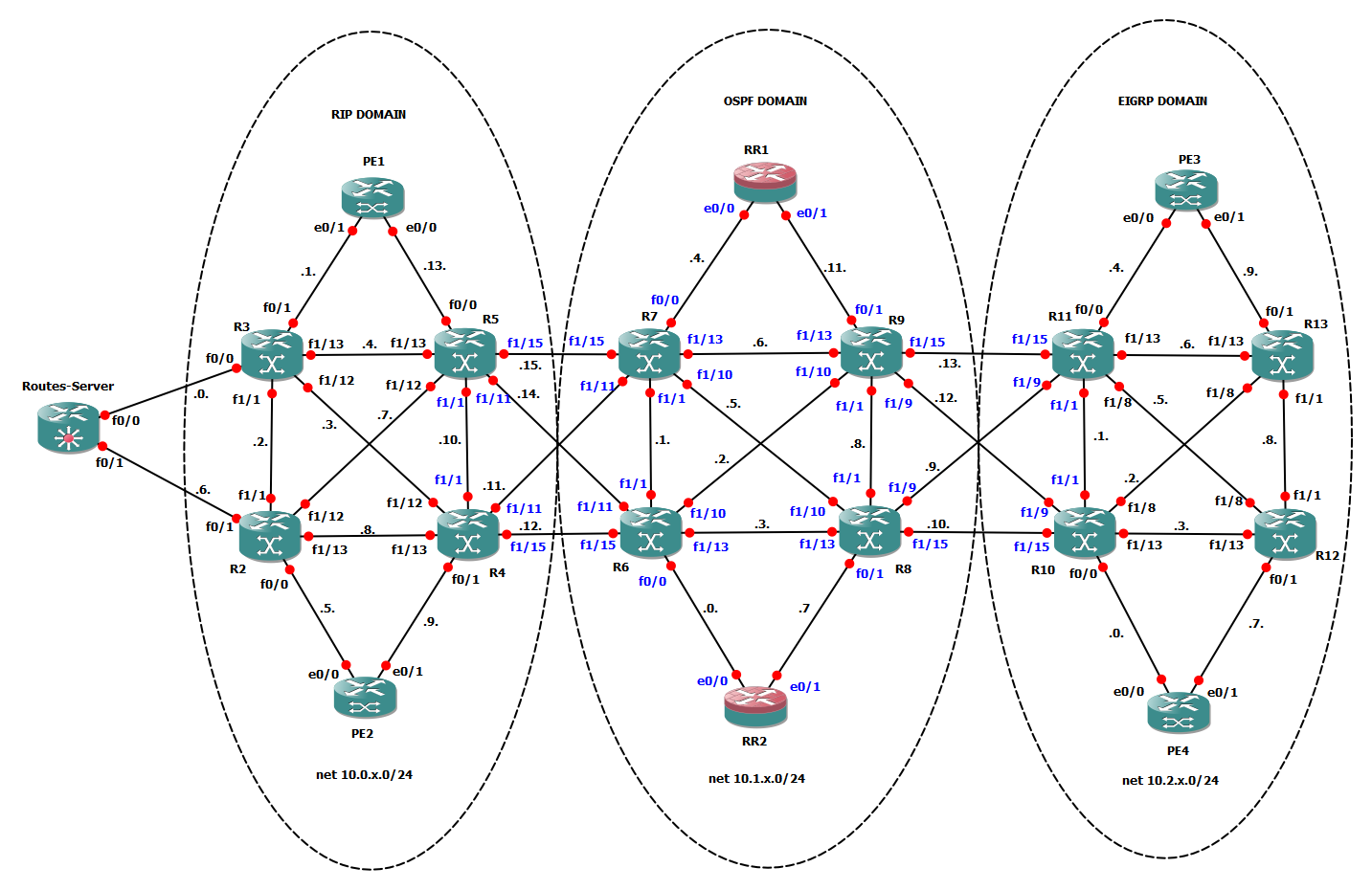
To do some tests I will use this topology already used in other topic:
NOTE: at each test I’ll clear configuration (access-lits, prefix-list, route-map, distribute-list) applied with previous test.
1. PASSIVE INTERFACE
Making passive an interface under EIGRP
R12(config)#router eigrp 2
R12(config-router)#passive-interface fa1/1
– Router stops sending hello packet out of interface –> neighborship is killed
– Previous peer on this interface receive a “goodbye” message:
R13# –> %DUAL-5-NBRCHANGE: IP-EIGRP(0) 2: Neighbor 10.2.8.12 (FastEthernet1/1) is down: Interface Goodbye received
– Router ignores received hello packets on this interface –> neighborship cannot be renegotiated
– Router stops sending out eigrp update on this interface
– Routers will not learn any eigrp update on this interface
– Router will keep network connected to the interface in its topology table and still advertises network in update going out from different interfaces
We can consider a passive interface a way to filter all updates coming in from a neighbour on that interface.
2. PREFIX-LIST
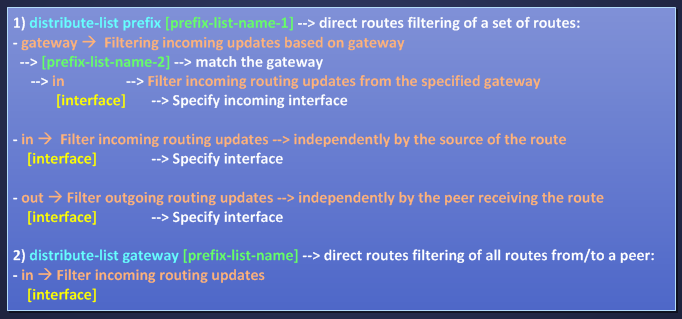
EIGRP can use a prefix-list for filtering-routes purpose calling it in these ways:
Option 1) gives me a very granular approach for filtering routes, for example I can filter a set of routes matched by a first prefix-list and filter them only for gateway matched by a second prefix-list also for a single interface. Let’s do an example:
PE3 and PE4 are injecting some routes into eigrp as external routes redistributing their connected loopbacks, for example on R10 i see:
R10#show ip route eigrp | i EX
D EX 32.4.0.0 [170/409600] via 10.2.0.254, 00:08:16, FastEthernet0/0
D EX 32.6.0.0 [170/409600] via 10.2.0.254, 00:08:16, FastEthernet0/0
D EX 33.11.11.0/24 [170/412160] via 10.2.2.13, 00:14:55, FastEthernet1/8
D EX 33.9.9.0/25 [170/409600] via 10.2.0.254, 00:08:16, FastEthernet0/0
D EX 33.9.9.128/25 [170/412160] via 10.2.2.13, 00:14:55, FastEthernet1/8
D EX 3.0.0.254 [170/412160] via 10.2.2.13, 00:14:55, FastEthernet1/8
D EX 4.0.0.254 [170/409600] via 10.2.0.254, 00:08:16, FastEthernet0/0
D EX 31.7.0.0/16 [170/412160] via 10.2.2.13, 00:14:55, FastEthernet1/8
D EX 31.5.5.0/24 [170/412160] via 10.2.2.13, 00:14:55, FastEthernet1/8
D EX 31.0.0.0/8 [170/409600] via 10.2.0.254, 00:08:16, FastEthernet0/0
D EX 30.2.2.128/26 [170/409600] via 10.2.0.254, 00:08:16, FastEthernet0/0
D EX 30.2.2.192/26 [170/409600] via 10.2.0.254, 00:08:16, FastEthernet0/0
D EX 30.1.1.248/29 [170/412160] via 10.2.2.13, 00:14:55, FastEthernet1/8
D EX 30.3.3.224/27 [170/412160] via 10.2.2.13, 00:14:55, FastEthernet1/8
On the eigrp domain border router (R10 and R11) I would receive all D EX routes from their connected PE and not from other eigrp peers and receive instead all internal eigrp networks 10.x.x.x from R12 and R13 and not from their PEs. One solution could be:
R10(config)#ip prefix-list DENY-TEN deny 10.0.0.0/8 ge 24
R10(config)#ip prefix-list DENY-TEN permit 0.0.0.0/0 le 32
R10(config)#ip prefix-list ALLOW-TEN permit 10.0.0.0/8 ge 24
R10(config)#ip prefix-list PE4-GW permit 10.2.0.254/32
R10(config)#ip prefix-list OTHER-GW permit 10.2.2.13/32
R10(config)#ip prefix-list OTHER-GW permit 10.2.3.12/32
R10#show run | s r e
router eigrp 2
network 10.2.0.0 0.0.0.255
network 10.2.2.0 0.0.0.255
network 10.2.3.0 0.0.0.255
distribute-list prefix DENY-TEN gateway PE4-GW in FastEthernet0/0
distribute-list prefix ALLOW-TEN gateway OTHER-GW in FastEthernet1/8
distribute-list prefix ALLOW-TEN gateway OTHER-GW in FastEthernet1/13
no auto-summary
with this eigrp configuration I’m telling R10:
– “deny networks 10.x.x.x and accept all other routes from PE4”
– “permit networks 10.x.x.x and discard all other routes from eigrp peers that are not PE4”
In each statement I specified interface option otherwise I cannot use more than one command with “in” direction. Verifying routing table:
All external networks are coming from PE4 (fa0/0) also the routes injected by PE3
R10#show ip route eigrp | i EX
D EX 32.4.0.0 [170/409600] via 10.2.0.254, 00:12:43, FastEthernet0/0
D EX 32.6.0.0 [170/409600] via 10.2.0.254, 00:12:43, FastEthernet0/0
D EX 33.11.11.0/24 [170/463360] via 10.2.0.254, 00:12:45, FastEthernet0/0
D EX 33.9.9.0/25 [170/409600] via 10.2.0.254, 00:12:43, FastEthernet0/0
D EX 33.9.9.128/25 [170/463360] via 10.2.0.254, 00:12:45, FastEthernet0/0
D EX 3.0.0.254 [170/463360] via 10.2.0.254, 00:12:45, FastEthernet0/0
D EX 4.0.0.254 [170/409600] via 10.2.0.254, 00:12:43, FastEthernet0/0
D EX 31.7.0.0/16 [170/463360] via 10.2.0.254, 00:12:45, FastEthernet0/0
D EX 31.5.5.0/24 [170/463360] via 10.2.0.254, 00:12:45, FastEthernet0/0
D EX 31.0.0.0/8 [170/409600] via 10.2.0.254, 00:12:43, FastEthernet0/0
D EX 30.2.2.128/26 [170/409600] via 10.2.0.254, 00:12:43, FastEthernet0/0
D EX 30.2.2.192/26 [170/409600] via 10.2.0.254, 00:12:43, FastEthernet0/0
D EX 30.1.1.248/29 [170/463360] via 10.2.0.254, 00:12:45, FastEthernet0/0
D EX 30.3.3.224/27 [170/463360] via 10.2.0.254, 00:12:45, FastEthernet0/0
R10#show ip route eigrp | b 10.0.0.0
10.0.0.0/8 is variably subnetted, 15 subnets, 2 masks
D 10.2.8.0/24 [90/30720] via 10.2.3.12, 00:15:44, FastEthernet1/13
[90/30720] via 10.2.2.13, 00:15:44, FastEthernet1/8
D 10.2.9.0/24 [90/284160] via 10.2.2.13, 00:25:54, FastEthernet1/8
D 10.2.4.0/24 [90/286720] via 10.2.3.12, 00:15:44, FastEthernet1/13
[90/286720] via 10.2.2.13, 00:15:44, FastEthernet1/8
D 10.2.5.0/24 [90/30720] via 10.2.3.12, 00:15:44, FastEthernet1/13
D 10.2.6.0/24 [90/30720] via 10.2.2.13, 00:25:54, FastEthernet1/8
D 10.2.7.0/24 [90/284160] via 10.2.3.12, 00:15:44, FastEthernet1/13
All internal networks are coming from R12 and R13. Do the same on R11.
Option “gateway” can be used as inbound filter blocking all update from a specific neighbor, for example on PE3 and PE4 I can block all routes eigrp coming in from R10 (10.2.0.10) and R11 (10.2.4.11) in this way:
PE3(config)# ip prefix-list R11-GW deny 10.2.4.11/32
PE3(config-router)#distribute-list gateway R11-GW in e0/0 –> match all incoming routes from gateway matched by prefix-list R11-GW, rule on prefix-list R11-GW is deny, so all routes will be denied.
As for RIP, the “out” keyword cannot be associated to the gateway option:
PE3(config-router)#distribute-list prefix FIRST gateway SECOND out e0/0
%EIGRP: Gateway not allowed with OUT in distribute-list cmd
PE3(config-router)#distribute-list gateway TEST out et0/0
%EIGRP: Gateway not allowed with OUT in distribute-list cmd
“out” keyword can be used for a set of routes on a single interface, for example if on PE3 and PE4 I had to block update about networks 30.x.x.x and 31.x.x.x on their interface e0/0 I can do:
PE3(config)#ip prefix-list NET-30-31 deny 30.0.0.0/7 ge 8
PE3(config)#ip prefix-list NET-30-31 permit 0.0.0.0/0 le 32
PE3(config)#router eigrp 2
PE3(config-router)#distribute-list prefix NET-30-31 out e0/0
PE4(config)#router eigrp 2
PE4(config-router)#distribute-list prefix NET-30-31 out e0/0
R10#show ip route eigrp | i EX –> no more 30/31.x.x.x
D EX 32.4.0.0 [170/409600] via 10.2.0.254, 00:56:47, FastEthernet0/0
D EX 32.6.0.0 [170/409600] via 10.2.0.254, 00:56:47, FastEthernet0/0
D EX 33.11.11.0/24 [170/463360] via 10.2.0.254, 00:56:47, FastEthernet0/0
D EX 33.9.9.0/25 [170/409600] via 10.2.0.254, 00:56:47, FastEthernet0/0
D EX 33.9.9.128/25 [170/463360] via 10.2.0.254, 00:56:47, FastEthernet0/0
D EX 3.0.0.254 [170/463360] via 10.2.0.254, 00:56:47, FastEthernet0/0
D EX 4.0.0.254 [170/409600] via 10.2.0.254, 00:56:47, FastEthernet0/0
R11#show ip route eigrp | i EX –> no more 30/31.x.x.x
D EX 32.4.0.0 [170/463360] via 10.2.4.254, 00:53:46, FastEthernet0/0
D EX 32.6.0.0 [170/463360] via 10.2.4.254, 00:53:46, FastEthernet0/0
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:53:44, FastEthernet0/0
D EX 33.9.9.0/25 [170/463360] via 10.2.4.254, 00:53:46, FastEthernet0/0
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:53:44, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:53:44, FastEthernet0/0
D EX 4.0.0.254 [170/463360] via 10.2.4.254, 00:53:46, FastEthernet0/0
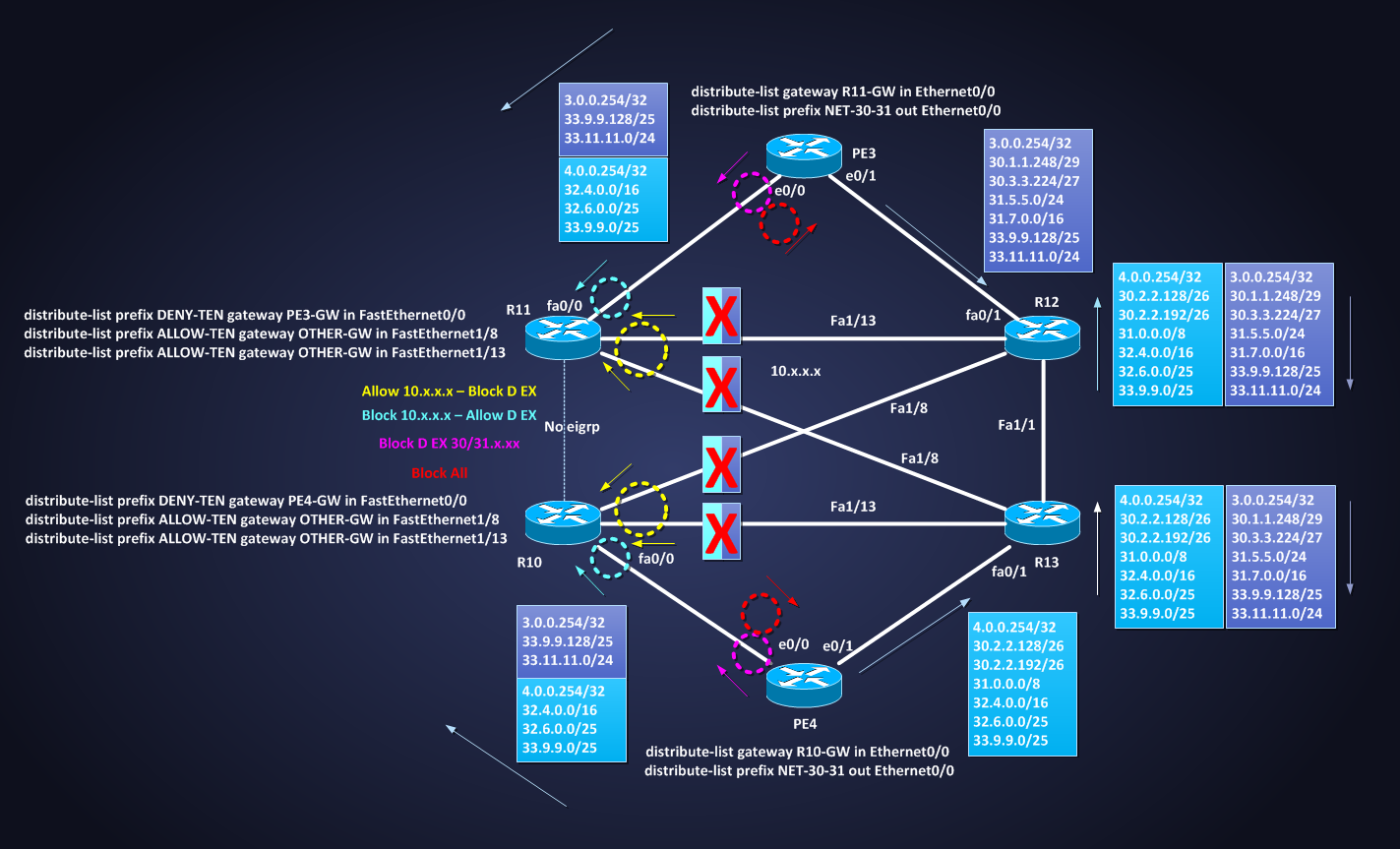
NOTE: I did a lot of filtering here just to show how prefix-list works with eigrp distribute-list, probably you can find a better solutions to get the same result. Following a picture showing all the filtering I did
3. STANDARD ACCESS-LIST
In eigrp a standard access-list can be invoked for filtering-routes purpose in two ways:
1) distribute-list [ext-ACL-number] in/out [interface]
–> direct routes filtering
2) route-map [route-map-name] permit/deny
match ip address [ext-ACL-number]
–> routes filtering during redistribution
Using a standard-ACL called by a distribute list, I can match only a portion of a network address to filter.
[ip-add][wilcard mask] = [net-add][wildcard mask]
For example R10 is knowing about networks 30.x.x.x via EIGRP:
R10#show ip route eigrp | b 30.0.0.0
30.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
D EX 30.2.2.128/26 [170/409600] via 10.2.0.254, 00:07:03, FastEthernet0/0
D EX 30.2.2.192/26 [170/409600] via 10.2.0.254, 00:07:03, FastEthernet0/0
D EX 30.1.1.248/29 [170/412160] via 10.2.2.13, 00:07:03, FastEthernet1/8
D EX 30.3.3.224/27 [170/412160] via 10.2.2.13, 00:07:03, FastEthernet1/8
I want block learning of these routes, I can do:
R10(config)#access-list 10 deny 30.0.0.0 0.255.255.255
R10(config)#access-list 10 permit any
R10(config)#router eigrp 2
R10(config-router)#distribute-list 10 in
R10#show ip route eigrp | b 30.0.0.0
[EMPTY OUTPUT]
R10#show ip route eigrp | i EX
D EX 32.4.0.0 [170/409600] via 10.2.0.254, 00:10:29, FastEthernet0/0
D EX 32.6.0.0 [170/409600] via 10.2.0.254, 00:10:29, FastEthernet0/0
D EX 33.11.11.0/24 [170/412160] via 10.2.2.13, 00:10:28, FastEthernet1/8
D EX 33.9.9.0/25 [170/409600] via 10.2.0.254, 00:10:29, FastEthernet0/0
D EX 33.9.9.128/25 [170/412160] via 10.2.2.13, 00:10:28, FastEthernet1/8
D EX 3.0.0.254 [170/412160] via 10.2.2.13, 00:10:28, FastEthernet1/8
D EX 4.0.0.254 [170/409600] via 10.2.0.254, 00:10:29, FastEthernet0/0
D EX 31.7.0.0/16 [170/412160] via 10.2.2.13, 00:10:28, FastEthernet1/8
D EX 31.5.5.0/24 [170/412160] via 10.2.2.13, 00:10:28, FastEthernet1/8
D EX 31.0.0.0/8 [170/409600] via 10.2.0.254, 00:10:29, FastEthernet0/0
Routes 30.x.x.x are gone.
EIGRP can invoke a standard-ACL by using a route-map referencing it for redistribution and filtering purpose.
For example I want do a controlled redistribution of connected Loopback on PE3:
PE3#show ip route | i C
Codes: L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
C 3.0.0.254 is directly connected, Loopback3
C 10.2.4.0/24 is directly connected, Ethernet0/0
C 10.2.9.0/24 is directly connected, Ethernet0/1
C 30.1.1.248/29 is directly connected, Loopback301
C 30.3.3.224/27 is directly connected, Loopback303
C 31.5.5.0/24 is directly connected, Loopback305
C 31.7.0.0/16 is directly connected, Loopback307
C 33.9.9.128/25 is directly connected, Loopback309
C 33.11.11.0/24 is directly connected, Loopback311
Let’s suppose we want redistribute only connected networks of Loopback 309 and 311 –> networks 33.x.x.x, I can do:
PE3(config)#access-list 33 permit 33.0.0.0 0.255.255.255
PE3(config)#route-map 33-INTO-EIGRP permit 10
PE3(config-route-map)#match ip address 33
PE3(config)#router eigrp 2
PE3(config-router)#redistribute connected route-map 33-INTO-EIGRP
on R11 for example I see:
R11#show ip route eigrp | i EX
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:20:48, FastEthernet0/0
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:20:48, FastEthernet0/0
NOTE: Standard ACL are very limited when used as routes filter because we cannot match mask length of the route. You can find more details about interaction between permit/deny rules of an ACL and permit/deny action of a route-map at this LINK
4. EXTENDED ACCESS-LIST
In eigrp an extended access-list can be invoked by for filtering-routes purpose in two ways:
1) distribute-list [ext-ACL-number] in/out [interface] –> direct routes filtering
2) route-map [route-map-name] permit/deny –> routes filtering during redistribution
match ip address [ext-ACL-number]
Here we must pay attention to the logic used (more details can be read at this LINK).
With option 1) since EIGRP is belonging to the family of IGP protocols, ext-ACL fields are interpreted by IOS in this way:
[source ip address][wildcard mask] = [ROUTE’S GATEWAY IP ADDRESS][wildcard mask] => match the ip address of the device to exit toward the route.
[destination ip address][wildcard mask] = [NETWORK ADDRESS][wildcard mask] => match the network portion of the ip prefix.
With option 2) fields of the ext-ACL are interpreted by IOS in this different ways:
[source ip address][wildcard mask] = [NETWORK ADDRESS][wildcard mask] => match a specific portion of the configured ADDRESS based on wildcard
[destination ip address][wildcard mask] = [NETWORK MASK][wildcard mask] => match a specific portion of the configured MASK based on wildcard => Mask Length
In other words, when using distribute-list + ext-ACL I can match gateway of the route and a portion of the network address based on a wildcard but I cannot match specific mask length. With route-map + ext-ACL I can match a portion of a network address and I can specifiy different mask length ranges.
Example 1) – distribute-list + ext-ACl
R11 is receiving these external EIGRP route from PE3 (10.2.4.254):
R11#show ip route eigrp | i EX
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
Let’s suppose we want filter on R10 some of these routes, for example the ones with first octet starting from 30.
————— NOTE —————-
As for RIP, an ext-ACL can be invoked by a distribute-list only if the ACL is an ext-numbered-ACL, if you try to call an ext-named-ACL you receive a warning of this type or a simliar one:
R11(config-router)#distribute-list [ext-named-ACL name] in fa0/0
Access-list type conflicts with prior definition
% This command only accepts named standard IP access-lists.
————- END NOTE —————
One solution could be:
R11(config)#access-list 100 deny ip 10.2.4.254 0.0.0.0 30.0.0.0 0.255.255.255 –> deny routes 30.x.x.x from gateway 10.2.4.254
R11(config)#access-list 100 permit ip any any
R11(config)#router eigrp 2
R11(config-router)#distribute-list 100 in fa0/0
R11#show run | s r e
router eigrp 2
network 10.2.4.0 0.0.0.255
network 10.2.5.0 0.0.0.255
network 10.2.6.0 0.0.0.255
distribute-list 100 in FastEthernet0/0
no auto-summary
R11#show ip route eigrp | i EX
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:16:48, FastEthernet0/0
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:16:48, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:16:48, FastEthernet0/0
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:16:48, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:16:48, FastEthernet0/0
D EX 30.1.1.248/29 [170/412160] via 10.2.6.13, 00:03:15, FastEthernet1/13
D EX 30.3.3.224/27 [170/412160] via 10.2.6.13, 00:03:15, FastEthernet1/13
Now networks 30.x.x.x are learned via 10.2.6.13 (R13) on fa1/13
Example 2) route-map + ext-ACL
Suppose now that PE3 instead of redistributing all connected Loopback must filter some of them (30.x.x.x and 31.x.x.x) . A solution could be filtering the redistribution with a route-map calling an extended ACL in this way:
PE3(config)#ip access-list extended NET-30-31
PE3(config-ext-nacl)#5 permit ip 30.0.0.0 1.255.255.255 0.0.0.0 255.255.255.255
ACL entry means –> check first 7 bits of the first octet 0001111|(0,1).any.any.any + any mask (wildcard all ones -> don’t check any bits)
PE3(config)#route-map NET-INTO-EIGRP deny 10
PE3(config-route-map)#match ip address NET-30-31
PE3(config)#route-map NET-INTO-EIGRP permit 20
PE3(config)#router eigrp 2
PE3(config-router)#redistribute connected route-map NET-INTO-EIGRP
PE3#show ip access-lists
Extended IP access list NET-30-31
5 permit ip 30.0.0.0 1.255.255.255 any (4 matches)
PE3#show ip eigrp topology | i P|Rconn
EIGRP-IPv4 Topology Table for AS(2)/ID(3.0.0.254)
Codes: P – Passive, A – Active, U – Update, Q – Query, R – Reply,
P 10.2.9.0/24, 1 successors, FD is 281600
P 3.0.0.254/32, 1 successors, FD is 128256
via Rconnected (128256/0)
P 10.2.2.0/24, 1 successors, FD is 284160
P 10.2.7.0/24, 2 successors, FD is 309760
P 10.2.8.0/24, 1 successors, FD is 284160
P 10.2.5.0/24, 1 successors, FD is 284160
P 10.2.0.0/24, 1 successors, FD is 309760
P 33.9.9.128/25, 1 successors, FD is 128256
via Rconnected (128256/0)
P 10.2.6.0/24, 2 successors, FD is 284160
P 10.2.4.0/24, 1 successors, FD is 281600
P 33.11.11.0/24, 1 successors, FD is 128256
via Rconnected (128256/0)
P 10.2.3.0/24, 2 successors, FD is 286720
Only 3.0.0.0/254 – 33.9.9.128/25 – 33.11.11.0/24 are redistributed, I can verify this looking at routes on R11:
R11#show ip route eigrp | i EX
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:32:50, FastEthernet0/0
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:32:50, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:32:50, FastEthernet0/0
NOTE: Net 30 was already filtered in incoming update from fa0/0, now these routes are gone together with net 31.x.x.x because PE3 does inject them no more.
————— NOTE —————-
Route-map permit/deny actions and ACL/prefix-list permit/deny rules interaction can be tricky, you can find more details at this LINK.
Here the route-map/ext-ACL interaction logic is: what is permitted by the ACL is considered by the route-map against the action (permit/deny) defined in its statement where the ACL is matched:
– ACL lets route-map consider networks 30/31.x.x.x/any-mask as a set of routes ruled by the deny action of the route-map so these routes are discarded. ACL deny every other routes, this means that route-map doesn’t consider this remaining set of routes for evaluation against this first statement.
– Route-Map takes the remaining (all other routes) routes to its second statement where it find an implicit match all (no match condition), since the action is permit route-map accepts these other routes.
————- END NOTE —————
5. OFFSET LISTS
An offset-list is a filtering tool when used as an extrema ratio. By default an offset-list is a tool used to INCREASE the metric of a route. Of course if we increase the metric so it reaches more than the maximum possible value, matched routes will be discarded as inaccessible (metric infinity).
Let’s think a moment about the infinity metric of EIGRP. With default K values EIGRP METRIC is:
METRIC = BANDWIDTH + DELAY – where: BANDWIDTH = [10^7/Minimum Bandwidth(Kbits/sec)]*256 and DELAY = Total-Delay(tens of usec)*256
The maximum metric value an eigrp route can have is 2^32 – 1 = 4294967295
Now let’s see how we can configure an OFFSET for a set of routes:
R11(config)#router eigrp 2
R11(config-router)#offset-list ?
<0-99> Access list of networks to apply offset (0 selects all networks) –> call a standard-ACL to match a set of routes – for example ACL “1”
<1300-1999> Access list of networks to apply offset (expanded range)
WORD Access-list name
R11(config-router)#offset-list 1 ?
in Perform offset on incoming updates –> apply the offset in
out Perform offset on outgoing updates –> apply the offset out
R11(config-router)#offset-list 1 in ?
<0-2147483647> Offset –> Define offset to apply
Here a question arises, with rip I can set an offset to a maximum of 16 hops filtering directly the matched routes. WIth EIGRP the maximum configurable offset is half the maximum metric an eigrp route can have; so with EIGRP I cannot directly filtering the route but I must do two separate things:
1) Apply an offset
2) Change some other metric so the route will be with metric infinity –> at least 4294967295 + 1 = 4294967296
R11(config-router)#offset-list 1 in “offset-value” [interface]
Let’s see an example. R11 is receiving external EIGRP routes from peer PE3:
R11#show ip route eigrp | i EX
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:00:14, FastEthernet0/0
I want match all these route and add the maximum possible offset. To match all routes I can use no access-list and simply tell router to match ACL 0:
R11(config)#router eigrp 2
R11(config-router)#offset-list 0 in 2147483647 fa0/0
NOTE: when playing with metrics, filters and so on eigrp neighborship resync:
%DUAL-5-NBRCHANGE: IP-EIGRP(0) 2: Neighbor 10.2.4.254 (FastEthernet0/0) is resync: route configuration changed
Applying the offset and having R11 alternate paths to the routes I see:
R11#show ip route eigrp | i EX
D EX 33.11.11.0/24 [170/412160] via 10.2.6.13, 00:01:10, FastEthernet1/13
D EX 33.9.9.128/25 [170/412160] via 10.2.6.13, 00:01:10, FastEthernet1/13
D EX 3.0.0.254 [170/412160] via 10.2.6.13, 00:01:10, FastEthernet1/13
D EX 31.7.0.0/16 [170/412160] via 10.2.6.13, 00:01:10, FastEthernet1/13
D EX 31.5.5.0/24 [170/412160] via 10.2.6.13, 00:01:10, FastEthernet1/13
D EX 30.1.1.248/29 [170/412160] via 10.2.6.13, 00:01:10, FastEthernet1/13
D EX 30.3.3.224/27 [170/412160] via 10.2.6.13, 00:01:10, FastEthernet1/13
So now R11 learns the route from R13. To keep things simple I apply another filter on R11 so it learns the external routes only from fa0/0:
R11(config)#ip prefix-list R12-R13-GW permit 10.2.5.12/32
R11(config)#ip prefix-list R12-R13-GW permit 10.2.6.13/32
R11(config)#ip prefix NET-TEN permit 10.0.0.0/8 ge 24
R11(config)#router eigrp 2
R11(config-router)#distribute-list prefix NET-TEN gateway R12-R13-GW in fa 1/8 –> permit 10.x.x.x from GW R12 or R13 incoming on fa1/8 | discard other routes
R11(config-router)#distribute-list prefix NET-TEN gateway R12-R13-GW in fa 1/13 –> permit 10.x.x.x from GW R12 or R13 incoming on fa1/8 | discard other routes
R11#show run | s r e
router eigrp 2
offset-list 0 in 2147483647 FastEthernet0/0
network 10.2.4.0 0.0.0.255
network 10.2.5.0 0.0.0.255
network 10.2.6.0 0.0.0.255
distribute-list prefix NET-TEN gateway R12-R13-GW in FastEthernet1/8
distribute-list prefix NET-TEN gateway R12-R13-GW in FastEthernet1/13
no auto-summary
Now I see again D EX routes from fa0/0 (PE3), I can see also the offset configured before:
R11#show ip route eigrp | i EX|0/0
D EX 33.11.11.0/24
[170/2147893247] via 10.2.4.254, 00:02:14, FastEthernet0/0
D EX 33.9.9.128/25
[170/2147893247] via 10.2.4.254, 00:02:14, FastEthernet0/0
D EX 3.0.0.254 [170/2147893247] via 10.2.4.254, 00:02:14, FastEthernet0/0
D EX 31.7.0.0/16 [170/2147893247] via 10.2.4.254, 00:02:14, FastEthernet0/0
D EX 31.5.5.0/24 [170/2147893247] via 10.2.4.254, 00:02:14, FastEthernet0/0
D EX 30.1.1.248/29
[170/2147893247] via 10.2.4.254, 00:02:14, FastEthernet0/0
D EX 30.3.3.224/27
[170/2147893247] via 10.2.4.254, 00:02:14, FastEthernet0/0
I can see that the offset is not enough to filter the route on fa0/0. I have to change some metric to get metric infinity. Metric before the offset was:
2147893247 – 2147483647 = 409600
R11#show ip eigrp topology 30.3.3.224/27
IP-EIGRP (AS 2): Topology entry for 30.3.3.224/27
State is Passive, Query origin flag is 1, 1 Successor(s), FD is 2147893247
Routing Descriptor Blocks:
10.2.4.254 (FastEthernet0/0), from 10.2.4.254, Send flag is 0x0
Composite metric is (2147893247/2147611903), Route is External
Vector metric:
Minimum bandwidth is 10000 Kbit
Total delay is 83892079 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 1
External data:
Originating router is 3.0.0.254
AS number of route is 0
External protocol is Connected, external metric is 0
Administrator tag is 0 (0x00000000)
From topology table I see Minimum bandwidth is 10000 Kbit and Total delay is 83892079 microseconds. I can play with one of this value.
NOTE: playing with bandwidth and delay can influence all the path for other routes. Take care.
NOTE: the value of total delay takes into account the configured offset – see below.
R11#show int fa0/0 | i BW
MTU 1500 bytes, BW 10000 Kbit/sec, DLY 1000 usec,
Bandwidth of fa0/0 is already = minimum, I can try to lower it but I prefer to change the delay, because BW can influence other protocols too.
R11(config)#int fa0/0
R11(config-if)#delay ?
<1-16777215> Throughput delay (tens of microseconds)
Let’s do some simple math: I want metric = 4294967296 – I have 2147893247 so I must add at least => 2147074049. We know that metric is :
METRIC = BANDWIDTH + DELAY – where: BANDWIDTH = [10^7/Minimum Bandwidth(Kbits/sec)]*256 and DELAY = Total-Delay(tens of usec)*256
2147074049/256 = Total-Delay(tens of usec) = 8387008,00390625 – adding this delay to the delay of fa0/0 (100 tens of usec)
R11(config)#int fa0/0
R11(config-if)#delay 8387108
R11#show ip eigrp topology 30.3.3.224/27
% IP-EIGRP (AS 2): Route not in topology table
NOTE: Once the route are gone, to let them come back is not enough restoring the delay of fa0/0, we must clear the neighborship to let PE3 resends the routes.
NOTE: In my opinion this is just a little game – offsetting routes in eigrp is good for increasing metric but not so good as a filter.
6. ADMININSTRATIVE DISTANCE
A simple method for filtering routing updates coming from a specific ip source is increasing the Administrative Distance up to 255.
In EIGRP we have two options to change AD of routes:
R11(config)#router eigrp 2
R11(config-router)#distance ?
<1-255> Administrative distance
eigrp IP-EIGRP distance
R11(config-router)#distance 255 ?
A.B.C.D IP Source address
R11(config-router)#distance 255 10.2.4.254 ?
A.B.C.D Wildcard bits
R11(config-router)#distance 255 10.2.4.254 0.0.0.0 ?
<1-99> IP Standard access list number
<1300-1999> IP Standard expanded access list number
WORD Standard access-list name
<cr>
First options is to set the distance for a specific or range of sources and for a set of routes specified by a standard-ACL. For example R11 is receiving these external EIGRP routes from PE3:
R11#show ip route eigrp | i EX
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:01:12, FastEthernet0/0
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:01:12, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:01:12, FastEthernet0/0
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:01:12, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:01:12, FastEthernet0/0
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:01:12, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:01:12, FastEthernet0/0
I could choose to discard only networks 30.x.x.x with this configuration:
R11(config)#access-list 30 permit 30.0.0.0 0.255.255.255
R11(config)#router eigrp 2
R11(config-router)#distance 255 10.2.4.254 0.0.0.0 30
R11#
%DUAL-5-NBRCHANGE: IP-EIGRP(0) 2: Neighbor 10.2.4.254 (FastEthernet0/0) is down: route configuration changed
%DUAL-5-NBRCHANGE: IP-EIGRP(0) 2: Neighbor 10.2.4.254 (FastEthernet0/0) is up: new adjacency
R11#show access-lists 30
Standard IP access list 30
10 permit 30.0.0.0, wildcard bits 0.255.255.255 (2 matches)
I see matching the routes against the ACL but I see no change:
R11#show ip route eigrp | i EX
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:03:53, FastEthernet0/0
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:03:53, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:03:53, FastEthernet0/0
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:03:53, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:03:53, FastEthernet0/0
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:03:53, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:03:53, FastEthernet0/0
Let’s change how PE3 injects the route into EIGRP, instead of passing the routes 30.x.x.x as Rconnect (redistribute connected on PE3) I set a network command under eigrp of PE3 for both two networks:
R11(config)#router eigrp 2
R11(config-router)#no distance 255 10.2.4.254 0.0.0.0 30
PE3#show run | s r e
router eigrp 2
network 10.2.4.0 0.0.0.255
network 10.2.9.0 0.0.0.255
network 30.1.1.248 0.0.0.7
network 30.3.3.224 0.0.0.31
redistribute connected
eigrp router-id 3.0.0.254
PE3#show ip eigrp topology | b 30
P 30.3.3.224/27, 1 successors, FD is 128256
via Connected, Loopback303
P 31.7.0.0/16, 1 successors, FD is 128256
via Rconnected (128256/0)
P 33.11.11.0/24, 1 successors, FD is 128256
via Rconnected (128256/0)
P 31.5.5.0/24, 1 successors, FD is 128256
via Rconnected (128256/0)
P 30.1.1.248/29, 1 successors, FD is 128256
via Connected, Loopback301
Now networks 30.x.x.x arrives to R1 as internal EIGRP routes:
R11#show ip route eigrp | b 30.0
30.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
D 30.1.1.248/29 [90/409600] via 10.2.4.254, 00:03:00, FastEthernet0/0
D 30.3.3.224/27 [90/409600] via 10.2.4.254, 00:03:20, FastEthernet0/0
If now I apply distance filter:
R11(config)#router eigrp 2
R11(config-router)#distance 255 10.2.4.254 0.0.0.0 30
R11#show ip route eigrp | b 30.0
R11#show ip eigrp topology 30.1.1.248/29
% IP-EIGRP (AS 2): Route not in topology table
R11#show ip eigrp topology 30.3.3.224/27
% IP-EIGRP (AS 2): Route not in topology table
I still see other external routes:
R11#show ip route eigrp | i EX
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:03:49, FastEthernet0/0
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:03:49, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:03:49, FastEthernet0/0
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:03:49, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:03:49, FastEthernet0/0
From this first test we can say that the command –> distance [distance-value] [source-ip] [wildcard] [std-ACL-number] works only for INTERNAL EIGRP ROUTES
Let’s check the second option available:
R11(config)#router eigrp 2
R11(config-router)#distance eigrp ?
<1-255> Distance for internal routes
R11(config-router)#distance eigrp 201 ?
<1-255> Distance for external routes
R11(config-router)#distance eigrp 201 230 ?
<cr>
R11(config-router)#distance eigrp 201 230
R11#show ip route eigrp
33.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
D EX 33.11.11.0/24 [230/409600] via 10.2.4.254, 00:00:06, FastEthernet0/0
D EX 33.9.9.128/25 [230/409600] via 10.2.4.254, 00:00:06, FastEthernet0/0
3.0.0.0/32 is subnetted, 1 subnets
D EX 3.0.0.254 [230/409600] via 10.2.4.254, 00:00:06, FastEthernet0/0
10.0.0.0/24 is subnetted, 7 subnets
D 10.2.9.0 [201/307200] via 10.2.4.254, 00:00:06, FastEthernet0/0
31.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
D EX 31.7.0.0/16 [230/409600] via 10.2.4.254, 00:00:06, FastEthernet0/0
D EX 31.5.5.0/24 [230/409600] via 10.2.4.254, 00:00:06, FastEthernet0/0
30.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
D 30.1.1.248/29 [201/409600] via 10.2.4.254, 00:00:06, FastEthernet0/0
D 30.3.3.224/27 [201/409600] via 10.2.4.254, 00:00:06, FastEthernet0/0
I changed all internal and external routes AD as configured: internal (201) external (230). What happens now if I add again the distance filter calling ACL 30?
R11#show run | s r e
router eigrp 2
network 10.2.4.0 0.0.0.255
network 10.2.5.0 0.0.0.255
network 10.2.6.0 0.0.0.255
distance eigrp 201 230
no auto-summary
R11#show access-lists 30
Standard IP access list 30
10 permit 30.0.0.0, wildcard bits 0.255.255.255
R11(config)#router eigrp 2
R11(config-router)#distance 255 10.2.4.254 0.0.0.0 30
R11#show ip route eigrp
33.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
D EX 33.11.11.0/24 [230/409600] via 10.2.4.254, 00:00:07, FastEthernet0/0
D EX 33.9.9.128/25 [230/409600] via 10.2.4.254, 00:00:07, FastEthernet0/0
3.0.0.0/32 is subnetted, 1 subnets
D EX 3.0.0.254 [230/409600] via 10.2.4.254, 00:00:07, FastEthernet0/0
10.0.0.0/24 is subnetted, 7 subnets
D 10.2.9.0 [201/307200] via 10.2.4.254, 00:00:07, FastEthernet0/0
31.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
D EX 31.7.0.0/16 [230/409600] via 10.2.4.254, 00:00:07, FastEthernet0/0
D EX 31.5.5.0/24 [230/409600] via 10.2.4.254, 00:00:07, FastEthernet0/0
I filtered again routes 30.x.x.x so to recap:
– distance filter –> distance [distance-value] [source-ip] [wildcard] [std-ACL-number]
— take precedence over distance eigrp [internal-AD-Value] [external-AD-value]
— but works only on internal eigrp routes [D] and not on external eigrp routes [D EX]
– to change AD of external eigrp route only available options is:
— using distance eigrp [internal-AD-Value] [external-AD-value] but we cannot select specific external routes – command works on all external routes.
– internal eigrp route can have:
— AD changed globally for all routes [distance eigrp command or distance-filter calling a std-ACL matching all internal routes]
— AD changed selectively for a set of route [distance-filter calling a std-ACL matching the set of routes]
– external eigrp route:
— AD can be changed for ALL routes or for NONE routes using distance eigrp command – no selection of routes available.
7. PER NEIGHBOR AD FILTERING
Per Neighbor AD filtering is a special case of AD filtering where we use the distance filter to match exactly the neighbor ip address and a set of its routes matched by an ACL.
8. ROUTE MAPS
EIGRP has on more filtering tool when compared to RIP – EIGRP can invoke a route-map directly for filtering purposes and not only when filtering during a redistribution. In other words, EIGRP can use a route-map in these ways:
1) distribute-list route-map [route-map-name] in/out [interface]
2) redistribute [protocol] route-map [route-map-name]
With option 1) we are enhancing the matching capabilities of a distribute-list [std-ACL(numbered/named), ext-ACL(numbered only), prefix-list, gateway] with the matching capabilities of a route-map:
R11(config)#route-map TEST permit 10
R11(config-route-map)#match ?
as-path Match BGP AS path list
clns CLNS information
community Match BGP community list
extcommunity Match BGP/VPN extended community list
interface Match first hop interface of route
ip IP specific information
ipv6 IPv6 specific information
length Packet length
local-preference Local preference for route
metric Match metric of route
mpls-label Match routes which have MPLS labels
nlri BGP NLRI type
policy-list Match IP policy list
route-type Match route-type of route
source-protocol Match source-protocol of route
tag Match tag of route
Of the above group of options some are specific to BGP protocol and others can be matched by many different protocols. Here I want do some tests when route-map is called by a distribute-list used as a route filter under eigrp. Before doing some tests I write here, as reference, routing table of R11 when no route-filter are in place, I show two outputs for external routes and internal routes.
R11#show ip route eigrp | i EX
D EX 32.4.0.0 [170/412160] via 10.2.5.12, 00:58:00, FastEthernet1/8
D EX 32.6.0.0 [170/412160] via 10.2.5.12, 00:58:00, FastEthernet1/8
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:29:04, FastEthernet0/0
D EX 33.9.9.0/25 [170/412160] via 10.2.5.12, 00:58:00, FastEthernet1/8
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:29:04, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:29:04, FastEthernet0/0
D EX 4.0.0.254 [170/412160] via 10.2.5.12, 00:58:00, FastEthernet1/8
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:29:04, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:29:04, FastEthernet0/0
D EX 31.0.0.0/8 [170/412160] via 10.2.5.12, 00:58:00, FastEthernet1/8
D EX 30.2.2.128/26 [170/412160] via 10.2.5.12, 00:58:00, FastEthernet1/8
D EX 30.2.2.192/26 [170/412160] via 10.2.5.12, 00:58:00, FastEthernet1/8
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:29:04, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:29:04, FastEthernet0/0
R11#show ip route eigrp | b 10.0.0.0
10.0.0.0/24 is subnetted, 14 subnets
D 10.2.8.0 [90/30720] via 10.2.6.13, 00:29:43, FastEthernet1/13
[90/30720] via 10.2.5.12, 00:29:43, FastEthernet1/8
D 10.2.9.0 [90/284160] via 10.2.6.13, 00:29:43, FastEthernet1/13
D 10.2.0.0 [90/286720] via 10.2.6.13, 00:29:43, FastEthernet1/13
[90/286720] via 10.2.5.12, 00:29:43, FastEthernet1/8
D 10.2.2.0 [90/30720] via 10.2.6.13, 00:29:43, FastEthernet1/13
D 10.2.3.0 [90/30720] via 10.2.5.12, 00:29:43, FastEthernet1/8
D 10.2.7.0 [90/284160] via 10.2.5.12, 00:29:43, FastEthernet1/8
TEST 1] match ip address
R11(config)#route-map FILTER deny 10
R11(config-route-map)#match ip ?
address Match address of route or match packet
next-hop Match next-hop address of route
route-source Match advertising source address of route
R11(config-route-map)#match ip address ?
<1-199> IP access-list number
<1300-2699> IP access-list number (expanded range)
WORD IP access-list name
prefix-list Match entries of prefix-lists
1a) match ip address [standard-ACL]
Suppose we want to filter all networks 30.x.x.x received by R11. One solution could be:
R11(config)#ip access-list standard NET-30
R11(config-std-nacl)#5 permit 30.0.0.0 0.255.255.255
R11(config)#route-map FILTER deny 10
R11(config-route-map)#match ip address NET-30 –> consider for denying what is matched by ACL NET-30
R11(config)#route-map FILTER permit 20 –> permit all that comes to this statement
R11(config)#router eigrp 2
R11(config-router)#distribute-list route-map FILTER in –> filter what is denied by the route-map
%DUAL-5-NBRCHANGE: IP-EIGRP(0) 2: Neighbor 10.2.4.254 (FastEthernet0/0) is resync: route configuration changed
%DUAL-5-NBRCHANGE: IP-EIGRP(0) 2: Neighbor 10.2.5.12 (FastEthernet1/8) is resync: route configuration changed
%DUAL-5-NBRCHANGE: IP-EIGRP(0) 2: Neighbor 10.2.6.13 (FastEthernet1/13) is resync: route configuration changed
R11#show ip route eigrp | i EX
D EX 32.4.0.0 [170/412160] via 10.2.5.12, 00:00:31, FastEthernet1/8
D EX 32.6.0.0 [170/412160] via 10.2.5.12, 00:00:31, FastEthernet1/8
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:00:31, FastEthernet0/0
D EX 33.9.9.0/25 [170/412160] via 10.2.5.12, 00:00:31, FastEthernet1/8
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:00:31, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:00:31, FastEthernet0/0
D EX 4.0.0.254 [170/412160] via 10.2.5.12, 00:00:31, FastEthernet1/8
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:00:31, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:00:31, FastEthernet0/0
D EX 31.0.0.0/8 [170/412160] via 10.2.5.12, 00:00:31, FastEthernet1/8
Networks 30 are gone. Here, one more time is important to understand the logic used by distribute-list route-map ACL:
– distribute-list is only a keyword to invoke a filter -> exclude what is denied by the filter, accept what is permitted by the filter
– route-map is the filter –> what a route-map does – permit/deny – depends on only its permit/deny action on each statement
– ACL –> determines what must be considered (permit) or not to be considered (deny) against the single route-map statement where it’s used
Here we are telling R11:
– deny (route-map deny 10) what ACL says to be considered (net 30.x.x.x) in first statement
– take things not considered (ACL deny) in first statement to the second route-map statement – no match means match all -> everything that comes to second statement will be permitted (route-map permit 20)
1b) match ip address [ext-ACL]
This option might be confusing. EIGRP is an IGP, so for what I learned here.
When an extended-ACL is used for filtering purpose,
distribute-list [ext-ACL] in/out
ACL fields are interpreted in this way:
A)
[source ip address][wildcard mask] = [ROUTE’S GATEWAY IP ADDRESS][wildcard mask] => match the ip address of the device to exit toward the route.
[destination ip address][wildcard mask] = [NETWORK ADDRESS][wildcard mask] => match the network portion of the ip prefix.
Field are interpreted in different way when ext-ACL is referenced by a route-map for example for redistribution:
redistribute [protocol] route-map [route-map-name] + route-map [route-map-name]: match ip address [ext-ACL]
B)
[source ip address][wildcard mask] = [NETWORK ADDRESS][wildcard mask] => match a specific portion of the configured ADDRESS based on wildcard
[destination ip address][wildcard mask] = [NETWORK MASK][wildcard mask] => match a specific portion of the configured MASK based on wildcard => Mask Length
Now the chain is: distribute-list –> route-map –> ext-ACL, so which of the two options we are using? Let’s check.
Suppose we want filter all routes starting with 30 or 31 with any net-mask:
R11(config)#ip access-list extended NET3031
R11(config-ext-nacl)#5 permit ip 30.0.0.0 1.255.255.255 0.0.0.0 255.255.255.255
I’m using logic A)
R11(config)#route-map FILTER deny 10
R11(config-route-map)#match ip address NET3031
R11(config)#route-map FILTER permit 20
R11(config-router)#do show run | s route-map
……………………
route-map FILTER deny 10
match ip address NET3031
route-map FILTER permit 20
Loooking at routing table for external networks:
R11#show ip route eigrp | i EX
D EX 32.4.0.0 [170/412160] via 10.2.5.12, 01:14:41, FastEthernet1/8
D EX 32.6.0.0 [170/412160] via 10.2.5.12, 01:14:41, FastEthernet1/8
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 01:14:41, FastEthernet0/0
D EX 33.9.9.0/25 [170/412160] via 10.2.5.12, 01:14:41, FastEthernet1/8
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 01:14:41, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 01:14:41, FastEthernet0/0
D EX 4.0.0.254 [170/412160] via 10.2.5.12, 01:14:41, FastEthernet1/8
Networks [30,31].x.x.x are filtered. So when a route-map match an ext-ACL the logic used is A) even if we are referencing all with a distribute-list under an IGP protocol. Using a route-map I extend filtering capabilities (without a route-map under eigrp I couldn’t use an ext-ACL for matching the mask length too)
1c) match ip address prefix-list [prefix-lits-name]
This option should be equivalent to the ext-ACL one, in other words we can match portion of network address and range of mask length. For example I can get the same result of example 1b) (filtering all [30,31].x.x.x any net-mask) with a prefix-list:
R11(config)#ip prefix-list NET3031 permit 30.0.0.0/7 le 32
R11(config)#route-map FILTER deny 10
R11(config-route-map)#match ip address prefix-list NET3031
R11(config)#route-map FILTER permit 20
R11(config)#do show run | s route-map
……………………
route-map FILTER deny 10
match ip address prefix-list NET3031
route-map FILTER permit 20
R11(config)#do show run | s r e
router eigrp 2
network 10.2.4.0 0.0.0.255
network 10.2.5.0 0.0.0.255
network 10.2.6.0 0.0.0.255
distribute-list route-map FILTER in
no auto-summary
Applying these config:
R11(config)#do show ip route eigrp | i EX
D EX 32.4.0.0 [170/412160] via 10.2.5.12, 01:38:12, FastEthernet1/8
D EX 32.6.0.0 [170/412160] via 10.2.5.12, 01:38:12, FastEthernet1/8
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 01:38:12, FastEthernet0/0
D EX 33.9.9.0/25 [170/412160] via 10.2.5.12, 01:38:12, FastEthernet1/8
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 01:38:12, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 01:38:12, FastEthernet0/0
D EX 4.0.0.254 [170/412160] via 10.2.5.12, 01:38:12, FastEthernet1/8
I’ve got the same results with a prefix-list too.
TEST 2] match ip next-hop
R11(config-route-map)#match ip next-hop ?
<1-99> IP access-list number
<1300-1999> IP access-list number (expanded range)
WORD IP standard access-list name
prefix-list Match entries of prefix-lists
R11 has 3 eigrp neighbors:
IP-EIGRP neighbors for process 2
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
2 10.2.6.13 Fa1/13 10 02:21:06 112 672 0 34
1 10.2.5.12 Fa1/8 14 02:22:23 108 648 0 68
0 10.2.4.254 Fa0/0 11 02:24:18 64 384 0 38
Next-hop we can match are the three addresses listed above, because with standard eigrp operation a router set always itself (next-hop-self) as next-hop router.
2a) match ip next-hop [std-ACL]
Suppose I wanted filter all networks coming from 10.2.5.12 (R12), I could do:
R11(config)#ip access-list standard R12
R11(config-std-nacl)#5 permit 10.2.5.12 0.0.0.0
R11(config)#route-map FILTER deny 10
R11(config-route-map)#match ip next-hop R12
R11(config)#route-map FILTER permit 20
R11(config-route-map)#set tag 11 –> I added a tag here, so route not considered by the first statement will receive a tag of 11
R11(config)#do show run | s r e
router eigrp 2
network 10.2.4.0 0.0.0.255
network 10.2.5.0 0.0.0.255
network 10.2.6.0 0.0.0.255
distribute-list route-map FILTER in
no auto-summary
R11#show ip route eigrp | i EX
D EX 32.4.0.0 [170/414720] via 10.2.6.13, 00:00:13, FastEthernet1/13
D EX 32.6.0.0 [170/414720] via 10.2.6.13, 00:00:13, FastEthernet1/13
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:00:13, FastEthernet0/0
D EX 33.9.9.0/25 [170/414720] via 10.2.6.13, 00:00:13, FastEthernet1/13
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:00:13, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:00:13, FastEthernet0/0
D EX 4.0.0.254 [170/414720] via 10.2.6.13, 00:00:13, FastEthernet1/13
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:00:13, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:00:13, FastEthernet0/0
D EX 31.0.0.0/8 [170/414720] via 10.2.6.13, 00:00:13, FastEthernet1/13
D EX 30.2.2.128/26 [170/414720] via 10.2.6.13, 00:00:13, FastEthernet1/13
D EX 30.2.2.192/26 [170/414720] via 10.2.6.13, 00:00:13, FastEthernet1/13
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:00:13, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:00:13, FastEthernet0/0
No routes are coming from R12 (10.2.5.12) any more. If I wanted now filter routes coming from R13 too, it’s enough adding its ip to the ACL. For readability reason I rename this ACL to NH:
R11(config)#ip access-list standard NH
R11(config-std-nacl)#permit 10.2.5.12 0.0.0.0
R11(config-std-nacl)#permit 10.2.6.13 0.0.0.0
R11#show run | s route-map
………………….
route-map FILTER deny 10
match ip next-hop NH
route-map FILTER permit 20
set tag 11
R11(config)#do show run | s r e
router eigrp 2
network 10.2.4.0 0.0.0.255
network 10.2.5.0 0.0.0.255
network 10.2.6.0 0.0.0.255
distribute-list route-map FILTER in
no auto-summary
R11#show ip route eigrp | i EX –> routes are coming only from PE3 (10.2.4.254) fa0/0
D EX 32.4.0.0 [170/463360] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 32.6.0.0 [170/463360] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 33.9.9.0/25 [170/463360] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 4.0.0.254 [170/463360] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 31.0.0.0/8 [170/463360] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 30.2.2.128/26 [170/463360] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 30.2.2.192/26 [170/463360] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:00:19, FastEthernet0/0
2b) match ip next-hop prefix-list [prefix-list-name]
I try to do the same test of denying route from 10.5.2.12 (R12), I call the prefix NH:
R11(config)#ip prefix-list NH permit 10.2.5.12/32 –> matching exactly ip of R12 – other config is the same of the first example with std-ACL
R11#show run | s route-map
route-map FILTER deny 10
match ip next-hop prefix-list NH
route-map FILTER permit 20
set tag 11
R11(config)#router eigrp 2
R11(config-router)#distribute-list route-map FILTER in
R11#show ip route eigrp | i 1/8
D EX 32.4.0.0 [170/412160] via 10.2.5.12, 00:04:38, FastEthernet1/8
D EX 32.6.0.0 [170/412160] via 10.2.5.12, 00:04:38, FastEthernet1/8
D EX 33.9.9.0/25 [170/412160] via 10.2.5.12, 00:04:38, FastEthernet1/8
D EX 4.0.0.254 [170/412160] via 10.2.5.12, 00:04:38, FastEthernet1/8
[90/30720] via 10.2.5.12, 00:04:38, FastEthernet1/8
[90/286720] via 10.2.5.12, 00:04:38, FastEthernet1/8
D 10.2.3.0 [90/30720] via 10.2.5.12, 00:04:38, FastEthernet1/8
D 10.2.7.0 [90/284160] via 10.2.5.12, 00:04:38, FastEthernet1/8
D EX 31.0.0.0/8 [170/412160] via 10.2.5.12, 00:04:38, FastEthernet1/8
D EX 30.2.2.128/26 [170/412160] via 10.2.5.12, 00:04:38, FastEthernet1/8
D EX 30.2.2.192/26 [170/412160] via 10.2.5.12, 00:04:38, FastEthernet1/8
I have filtered nothing, all the routes are matched by the second route-map statement that permits all and set tag 11:
R11#show ip route 30.2.2.192
Routing entry for 30.2.2.192/26
Known via “eigrp 2”, distance 170, metric 412160
Tag 11, type external
Redistributing via eigrp 2
Last update from 10.2.5.12 on FastEthernet1/8, 00:06:00 ago –> 10.2.5.12 not denied
Routing Descriptor Blocks:
* 10.2.5.12, from 10.2.5.12, 00:06:00 ago, via FastEthernet1/8
Route metric is 412160, traffic share count is 1
Total delay is 6100 microseconds, minimum bandwidth is 10000 Kbit
Reliability 255/255, minimum MTU 1500 bytes
Loading 1/255, Hops 2
Route tag 11 –> tagged by route-map
I change the prefix to deny:
R11(config)#ip prefix-list NH deny 10.2.5.12/32
I re-apply the filter:
R11#
%DUAL-5-NBRCHANGE: IP-EIGRP(0) 2: Neighbor 10.2.4.254 (FastEthernet0/0) is resync: route configuration changed
%DUAL-5-NBRCHANGE: IP-EIGRP(0) 2: Neighbor 10.2.5.12 (FastEthernet1/8) is resync: route configuration changed
%DUAL-5-NBRCHANGE: IP-EIGRP(0) 2: Neighbor 10.2.6.13 (FastEthernet1/13) is resync: route configuration changed
R11#show ip route eigrp | i EX
D EX 32.4.0.0 [170/412160] via 10.2.5.12, 00:00:08, FastEthernet1/8
D EX 32.6.0.0 [170/412160] via 10.2.5.12, 00:00:08, FastEthernet1/8
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:00:08, FastEthernet0/0
D EX 33.9.9.0/25 [170/412160] via 10.2.5.12, 00:00:08, FastEthernet1/8
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:00:08, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:00:08, FastEthernet0/0
D EX 4.0.0.254 [170/412160] via 10.2.5.12, 00:00:08, FastEthernet1/8
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:00:08, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:00:08, FastEthernet0/0
D EX 31.0.0.0/8 [170/412160] via 10.2.5.12, 00:00:08, FastEthernet1/8
D EX 30.2.2.128/26 [170/412160] via 10.2.5.12, 00:00:08, FastEthernet1/8
D EX 30.2.2.192/26 [170/412160] via 10.2.5.12, 00:00:08, FastEthernet1/8
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:00:08, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:00:08, FastEthernet0/0
Nothing changes. I configure only a permit all to the prefix, so I should deny everything:
R11(config)#no ip prefix-list NH
R11(config)#ip prefix-list NH permit 0.0.0.0/32
R11#show ip route eigrp
32.0.0.0/16 is subnetted, 2 subnets
D EX 32.4.0.0 [170/412160] via 10.2.5.12, 00:00:16, FastEthernet1/8
D EX 32.6.0.0 [170/412160] via 10.2.5.12, 00:00:16, FastEthernet1/8
33.0.0.0/8 is variably subnetted, 3 subnets, 2 masks
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:00:16, FastEthernet0/0
D EX 33.9.9.0/25 [170/412160] via 10.2.5.12, 00:00:16, FastEthernet1/8
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:00:16, FastEthernet0/0
3.0.0.0/32 is subnetted, 1 subnets
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:00:16, FastEthernet0/0
4.0.0.0/32 is subnetted, 1 subnets
D EX 4.0.0.254 [170/412160] via 10.2.5.12, 00:00:16, FastEthernet1/8
10.0.0.0/24 is subnetted, 14 subnets
D 10.2.8.0 [90/30720] via 10.2.6.13, 00:00:16, FastEthernet1/13
[90/30720] via 10.2.5.12, 00:00:16, FastEthernet1/8
D 10.2.9.0 [90/284160] via 10.2.6.13, 00:00:16, FastEthernet1/13
D 10.2.0.0 [90/286720] via 10.2.6.13, 00:00:16, FastEthernet1/13
[90/286720] via 10.2.5.12, 00:00:17, FastEthernet1/8
D 10.2.2.0 [90/30720] via 10.2.6.13, 00:00:17, FastEthernet1/13
D 10.2.3.0 [90/30720] via 10.2.5.12, 00:00:17, FastEthernet1/8
D 10.2.7.0 [90/284160] via 10.2.5.12, 00:00:17, FastEthernet1/8
31.0.0.0/8 is variably subnetted, 3 subnets, 3 masks
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:00:17, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:00:17, FastEthernet0/0
D EX 31.0.0.0/8 [170/412160] via 10.2.5.12, 00:00:19, FastEthernet1/8
30.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
D EX 30.2.2.128/26 [170/412160] via 10.2.5.12, 00:00:19, FastEthernet1/8
D EX 30.2.2.192/26 [170/412160] via 10.2.5.12, 00:00:19, FastEthernet1/8
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:00:19, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:00:19, FastEthernet0/0
Nothing changes.
Let’s do the same with a standard ACL ALL-NH permitting everything:
R11(config)#ip access-list standard ALL-NH
R11(config-std-nacl)#permit any
R11#show run | s route-map
route-map FILTER deny 10
match ip next-hop ALL-NH
route-map FILTER permit 20
set tag 11
R11(config)#router eigrp 2
R11(config-router)#distribute-list route-map FILTER in
Now I filtered all routes:
R11#show ip eigrp topology –> only connected networks
IP-EIGRP Topology Table for AS(2)/ID(11.11.11.11)
Codes: P – Passive, A – Active, U – Update, Q – Query, R – Reply,
r – reply Status, s – sia Status
P 10.2.4.0/24, 1 successors, FD is 281600
via Connected, FastEthernet0/0
P 10.2.5.0/24, 1 successors, FD is 28160
via Connected, FastEthernet1/8
P 10.2.6.0/24, 1 successors, FD is 28160
via Connected, FastEthernet1/13
So from this test I can conclude that ip next-hop doesn’t support prefix-list.
———— NOTE —————-
Let’s review the options:
R11(config-route-map)#match ip next-hop ?
<1-99> IP access-list number
<1300-1999> IP access-list number (expanded range)
WORD IP standard access-list name
prefix-list Match entries of prefix-lists
Here I can see that ext-ACL are not supported, since route-map uses ext-ACL and prefix-list with the same logic the presence of the prefix-list option under the command should install into you a BIG WARNING. If you read carefully also the “return” [cr] option doesn’t make too match sense to me. So when you want to use ip next-hop as matching criteria DO USE a STANDARD ACL. Route-Map are complex general tool available under many protocols and in many context, but even if IOS gives you the possibility to configure something, this doesn’t mean that everything is supported.
TEST 3] match ip route-source
What is true for the option next-hop is true also for the option route-source, because in standard eigrp operation the next-hop is always equal to the ip address of the router originating the update because every eigrp router sets next-hop-self. So if you want use route-source, one more time, use a std-ACL. Here I want review a specific option related to eigrp protocol:
R11(config-route-map)#match ip route-source redistribution-source
Looking at external eigrp routes learned by R11:
R11#show ip route eigrp | i EX
D EX 32.4.0.0 [170/412160] via 10.2.5.12, 00:07:20, FastEthernet1/8
D EX 32.6.0.0 [170/412160] via 10.2.5.12, 00:07:20, FastEthernet1/8
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:07:20, FastEthernet0/0
D EX 33.9.9.0/25 [170/412160] via 10.2.5.12, 00:07:20, FastEthernet1/8
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:07:20, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:07:20, FastEthernet0/0
D EX 4.0.0.254 [170/412160] via 10.2.5.12, 00:07:20, FastEthernet1/8
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:07:20, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:07:20, FastEthernet0/0
D EX 31.0.0.0/8 [170/412160] via 10.2.5.12, 00:07:20, FastEthernet1/8
D EX 30.2.2.128/26 [170/412160] via 10.2.5.12, 00:07:20, FastEthernet1/8
D EX 30.2.2.192/26 [170/412160] via 10.2.5.12, 00:07:20, FastEthernet1/8
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:07:20, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:07:20, FastEthernet0/0
All these routes are injected into eigrp by eihter PE3 or PE4:
R11#show ip eigrp topology 30.2.2.192/26
IP-EIGRP (AS 2): Topology entry for 30.2.2.192/26
State is Passive, Query origin flag is 1, 1 Successor(s), FD is 412160
Routing Descriptor Blocks:
10.2.5.12 (FastEthernet1/8), from 10.2.5.12, Send flag is 0x0
Composite metric is (412160/409600), Route is External
Vector metric:
Minimum bandwidth is 10000 Kbit
Total delay is 6100 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 2
External data:
Originating router is 4.0.0.254
AS number of route is 0
External protocol is Connected, external metric is 0
Administrator tag is 0 (0x00000000)
10.2.6.13 (FastEthernet1/13), from 10.2.6.13, Send flag is 0x0
Composite metric is (414720/412160), Route is External
Vector metric:
Minimum bandwidth is 10000 Kbit
Total delay is 6200 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 3
External data:
Originating router is 4.0.0.254
AS number of route is 0
External protocol is Connected, external metric is 0
Administrator tag is 0 (0x00000000)
R11#show ip eigrp topology 30.3.3.224/27
IP-EIGRP (AS 2): Topology entry for 30.3.3.224/27
State is Passive, Query origin flag is 1, 1 Successor(s), FD is 409600
Routing Descriptor Blocks:
10.2.4.254 (FastEthernet0/0), from 10.2.4.254, Send flag is 0x0
Composite metric is (409600/128256), Route is External
Vector metric:
Minimum bandwidth is 10000 Kbit
Total delay is 6000 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 1
External data:
Originating router is 3.0.0.254
AS number of route is 0
External protocol is Connected, external metric is 0
Administrator tag is 0 (0x00000000)
10.2.6.13 (FastEthernet1/13), from 10.2.6.13, Send flag is 0x0
Composite metric is (412160/409600), Route is External
Vector metric:
Minimum bandwidth is 10000 Kbit
Total delay is 6100 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 2
External data:
Originating router is 3.0.0.254
AS number of route is 0
External protocol is Connected, external metric is 0
Administrator tag is 0 (0x00000000)
Option “route-source redistribution-source” allows to match the ip address defined in Originating Router field of the External Data section of an external eigrp route. In this case eigrp-router-id of PE3 and PE4 are 3.0.0.254 and 4.0.0.254. If I wanted filter all external routes injected by PE4 I could do:
R11(config)#ip access-list standard PE4
R11(config-std-nacl)#5 permit 4.0.0.254 0.0.0.0
R11#show run | s route-map
route-map FILTER deny 10
match ip route-source redistribution-source PE4
route-map FILTER permit 20
R11(config)#router eigrp 2
R11(config-router)#distribute-list route-map FILTER in
R11#show ip route eigrp | i EX –> only external route with Originating Router 3.0.0.254 remains in routing table
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:29:37, FastEthernet0/0
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:29:37, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:29:37, FastEthernet0/0
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:29:37, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:29:37, FastEthernet0/0
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:29:37, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:29:37, FastEthernet0/0
TEST 4] match route-type
Another useful option is matching the type of the route INTERNAL or EXTERNAL. As an example, let’s filter out all external routes from routing table of R11:
R11#show run | s route-map
route-map FILTER deny 10
match route-type external
route-map FILTER permit 20
R11(config)#router eigrp 2
R11(config-router)#distribute-list route-map FILTER in
R11#show ip route eigrp
10.0.0.0/24 is subnetted, 14 subnets
D 10.2.8.0 [90/30720] via 10.2.6.13, 00:46:49, FastEthernet1/13
[90/30720] via 10.2.5.12, 00:46:49, FastEthernet1/8
D 10.2.9.0 [90/284160] via 10.2.6.13, 00:46:49, FastEthernet1/13
D 10.2.0.0 [90/286720] via 10.2.6.13, 00:46:10, FastEthernet1/13
[90/286720] via 10.2.5.12, 00:46:10, FastEthernet1/8
D 10.2.2.0 [90/30720] via 10.2.6.13, 00:46:49, FastEthernet1/13
D 10.2.3.0 [90/30720] via 10.2.5.12, 00:46:49, FastEthernet1/8
D 10.2.7.0 [90/284160] via 10.2.5.12, 00:46:49, FastEthernet1/8
using route-map as matching filter gives great flexibility, for example If now I want filter only external router coming from R12:
R11(config)#ip access-li sta R12
R11(config-std-nacl)#5 permit 10.2.5.12 0.0.0.0
R11#show run | s route-map
………………..
R11#show run | s route-map
route-map FILTER deny 10
match ip route-source R12
match route-type external
route-map FILTER permit 20
R11#show ip route eigrp | i EX –> Filtered external routes coming from R12 (fa1/8)
D EX 32.4.0.0 [170/414720] via 10.2.6.13, 00:00:10, FastEthernet1/13
D EX 32.6.0.0 [170/414720] via 10.2.6.13, 00:00:10, FastEthernet1/13
D EX 33.11.11.0/24 [170/409600] via 10.2.4.254, 00:03:08, FastEthernet0/0
D EX 33.9.9.0/25 [170/414720] via 10.2.6.13, 00:00:10, FastEthernet1/13
D EX 33.9.9.128/25 [170/409600] via 10.2.4.254, 00:03:08, FastEthernet0/0
D EX 3.0.0.254 [170/409600] via 10.2.4.254, 00:03:08, FastEthernet0/0
D EX 4.0.0.254 [170/414720] via 10.2.6.13, 00:00:10, FastEthernet1/13
D EX 31.7.0.0/16 [170/409600] via 10.2.4.254, 00:03:08, FastEthernet0/0
D EX 31.5.5.0/24 [170/409600] via 10.2.4.254, 00:03:08, FastEthernet0/0
D EX 31.0.0.0/8 [170/414720] via 10.2.6.13, 00:00:10, FastEthernet1/13
D EX 30.2.2.128/26 [170/414720] via 10.2.6.13, 00:00:10, FastEthernet1/13
D EX 30.2.2.192/26 [170/414720] via 10.2.6.13, 00:00:10, FastEthernet1/13
D EX 30.1.1.248/29 [170/409600] via 10.2.4.254, 00:03:08, FastEthernet0/0
D EX 30.3.3.224/27 [170/409600] via 10.2.4.254, 00:03:08, FastEthernet0/0
R11#show ip route eigrp | b 10.0.0.0 –> no other route from R12 are filtered.
10.0.0.0/24 is subnetted, 14 subnets
D 10.2.8.0 [90/30720] via 10.2.6.13, 01:09:38, FastEthernet1/13
[90/30720] via 10.2.5.12, 01:09:38, FastEthernet1/8
D 10.2.9.0 [90/284160] via 10.2.6.13, 01:09:38, FastEthernet1/13
D 10.2.0.0 [90/286720] via 10.2.6.13, 01:08:59, FastEthernet1/13
[90/286720] via 10.2.5.12, 01:08:59, FastEthernet1/8
D 10.2.2.0 [90/30720] via 10.2.6.13, 01:09:38, FastEthernet1/13
D 10.2.3.0 [90/30720] via 10.2.5.12, 01:09:38, FastEthernet1/8
D 10.2.7.0 [90/284160] via 10.2.5.12, 01:09:38, FastEthernet1/8
TEST 5] match source protocol
R11#show ip eigrp topology 30.3.3.224/27
IP-EIGRP (AS 2): Topology entry for 30.3.3.224/27
State is Passive, Query origin flag is 1, 1 Successor(s), FD is 409600
Routing Descriptor Blocks:
10.2.4.254 (FastEthernet0/0), from 10.2.4.254, Send flag is 0x0
Composite metric is (409600/128256), Route is External
Vector metric:
Minimum bandwidth is 10000 Kbit
Total delay is 6000 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 1
External data:
Originating router is 3.0.0.254
AS number of route is 0
External protocol is Connected, external metric is 0 –> source protocol
Administrator tag is 0 (0x00000000)
10.2.6.13 (FastEthernet1/13), from 10.2.6.13, Send flag is 0x0
Composite metric is (412160/409600), Route is External
Vector metric:
Minimum bandwidth is 10000 Kbit
Total delay is 6100 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 2
External data:
Originating router is 3.0.0.254
AS number of route is 0
External protocol is Connected, external metric is 0 –> source protocol
Administrator tag is 0 (0x00000000)
R11#show run | s route-map
route-map FILTER deny 10
match source-protocol connected
route-map FILTER permit 20
R11#show run | s r e
router eigrp 2
network 10.2.4.0 0.0.0.255
network 10.2.5.0 0.0.0.255
network 10.2.6.0 0.0.0.255
distribute-list route-map FILTER in
no auto-summary
R11#show ip route eigrp
10.0.0.0/24 is subnetted, 14 subnets
D 10.2.8.0 [90/30720] via 10.2.6.13, 01:42:58, FastEthernet1/13
[90/30720] via 10.2.5.12, 01:42:58, FastEthernet1/8
D 10.2.9.0 [90/284160] via 10.2.6.13, 01:42:58, FastEthernet1/13
D 10.2.0.0 [90/286720] via 10.2.6.13, 01:42:19, FastEthernet1/13
[90/286720] via 10.2.5.12, 01:42:19, FastEthernet1/8
D 10.2.2.0 [90/30720] via 10.2.6.13, 01:42:58, FastEthernet1/13
D 10.2.3.0 [90/30720] via 10.2.5.12, 01:42:58, FastEthernet1/8
D 10.2.7.0 [90/284160] via 10.2.5.12, 01:42:58, FastEthernet1/8
Again I filtered all external routes because all external routes in this case are injected by redistributing connected on PE3 and P4, more in general I can match the protocol from witch the route are redistributed into eigrp.
9. PER NEIGHBOR PREFIX LIMIT AND REDISTRIBUTION PREFIX LIMIT
These options are specific to an MPLS/VPN environment. Under ipv4 address family of each vrf can be specified the maximum number of prefix limit learned by a peer. The same can be configured for redistribution purpose.
– router eigrp as-number
– address-family ipv4 [unicast] vrf vrf-name
– neighbor ip-address maximum-prefix maximum [threshold] [warning-only]
– neighbor maximum-prefix maximum [threshold] [[dampened] [reset-time minutes] [restart minutes] [restart-count number] | [warning-only]]
– router eigrp as-number
– address-family ipv4 [unicast] vrf vrf-name
– redistribute maximum-prefix maximum [threshold] [[dampened] [reset-time minutes] [restart minutes] [restart-count number] | [warning-only]]
Here the Cisco link where to find more detailed info.