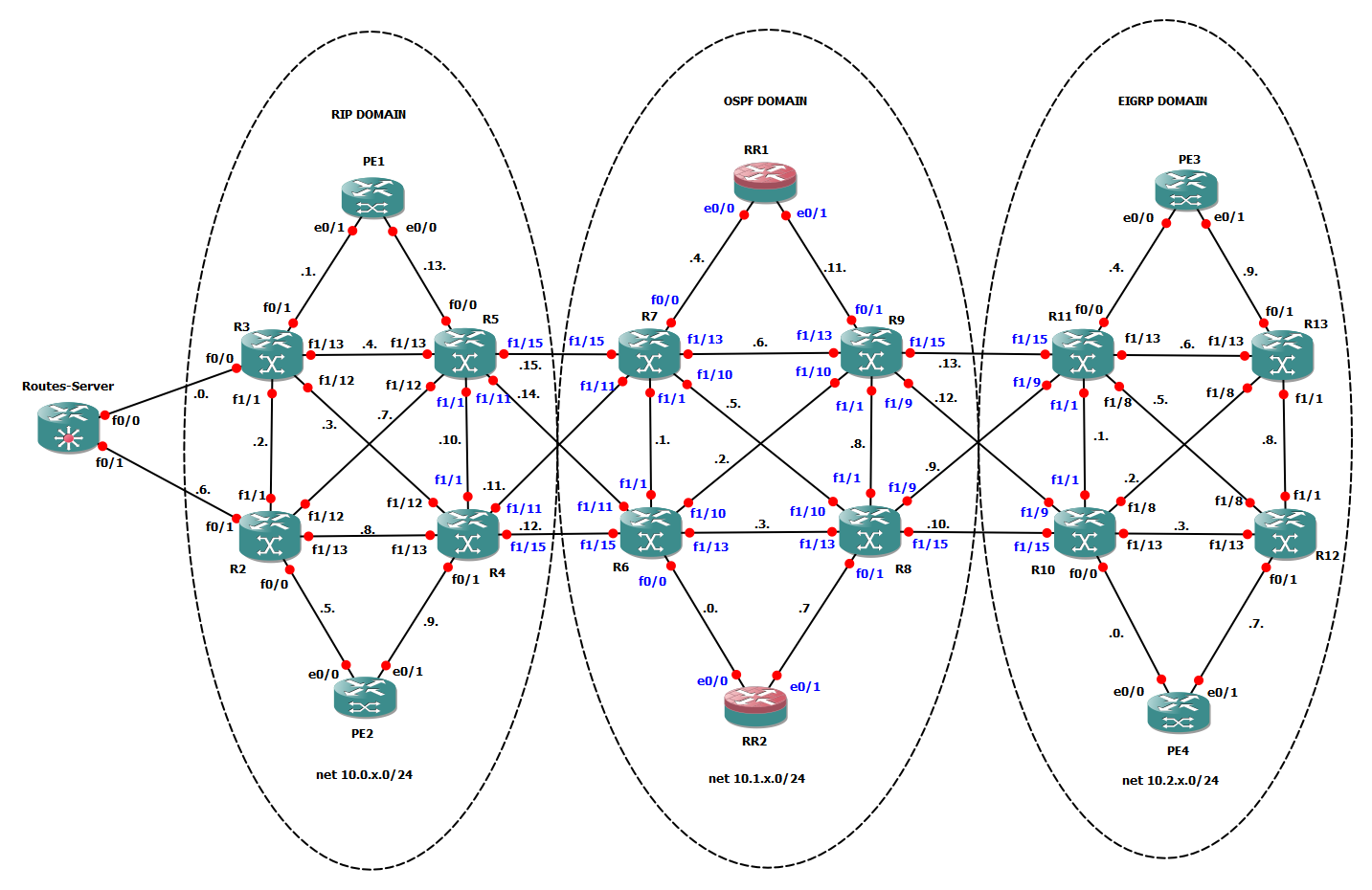
Here I want to review route filtering techniques common to different routing protocols. Topology I will refer to is this one:
 There are many techniques to filter routes from a source via a specific routing protocol. Some of them are specific to one routing protocols others are common to all protocols. Generally speaking we can say that filtering techniques can be listed as:
There are many techniques to filter routes from a source via a specific routing protocol. Some of them are specific to one routing protocols others are common to all protocols. Generally speaking we can say that filtering techniques can be listed as:
– Access-List (Standard/Extended)
– Prefix-List
– Route-Map
– Distribute-List
Some other features can be seen as indirect filtering techniques:
– Passive Interface
– Default route
– Static Route
Let’s approach these filtering techniques.
Before starting I activate the Route-Server. This device acts like a Route Generator, to generate randomly 100 Loopbacks I used a tcl script I found here. Generated Loopbacks are all in public address space and have random netmask lenght too, so I find also supernent like
Routes-Server#show ip route | i 181
C 181.172.0.0/15 is directly connected, Loopback10060
Route-Server is connected by RIP (ok not a good solution to inject many routes in a routing domain, but here helps me with the test), RIP is configured with default autosummarization,
router rip
version 2
redistribute connected
network 10.0.0.0
so R2 and R3 are receiving via RIP all the Route-Server’s connected networks summarized at classful network boundary because when Route-Server advertises routes it crosses links configured with different classful networks f0/0: 10.0.0.0/24 (classful 10.0.0.0/8) and fa0/1:10.0.6.0/24 (classful 10.0.0.0/8). For example:
Routes-Server#show ip route | b 104.0.0.0/8
104.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 104.219.202.48/29 is directly connected, Loopback10053
C 104.54.143.0/24 is directly connected, Loopback10100
R2#show ip route 104.0.0.0
Routing entry for 104.0.0.0/8
Known via “rip”, distance 120, metric 1
Redistributing via rip
Last update from 10.0.6.254 on FastEthernet0/1, 00:00:13 ago
Routing Descriptor Blocks:
* 10.0.6.254, from 10.0.6.254, 00:00:13 ago, via FastEthernet0/1
Route metric is 1, traffic share count is 1
R3#show ip route 104.0.0.0
Routing entry for 104.0.0.0/8
Known via “rip”, distance 120, metric 1
Redistributing via rip
Last update from 10.0.0.254 on FastEthernet0/0, 00:00:13 ago
Routing Descriptor Blocks:
* 10.0.0.254, from 10.0.0.254, 00:00:13 ago, via FastEthernet0/0
Route metric is 1, traffic share count is 1
$$$$$$$ ACCESS-LIST $$$$$$$
As first example suppose I want to filter network 104.0.0.0/8 entering R2 using an Access-List. Steps are:
1] Create a standard access-list to match the route net 104.0.0.0/8
R2(config)#ip access-list standard NET-104
R2(config-std-nacl)#5 deny 104.0.0.0 0.255.255.255
R2(config-std-nacl)#20 permit any
R2#show run | s ip acc
ip access-list standard NET-104
deny 104.0.0.0 0.255.255.255
permit any
R2#show ip access-list
Standard IP access list NET-104
5 deny 104.0.0.0, wildcard bits 0.255.255.255 (43 matches)
20 permit any (4042 matches)
2] Apply the ACL to RIP Routing Protocol
To apply an ACL to the routing process I must use a distribute-list command in this way:
R2(config)#router rip
R2(config-router)#distribute-list ?
<1-199> IP access list number
<1300-2699> IP expanded access list number
WORD Access-list name
gateway Filtering incoming updates based on gateway
prefix Filter prefixes in routing update
R2(config-router)#distribute-list NET-104 in
R2#show run | s r r
router rip
version 2
network 10.0.0.0
distribute-list NET-104 in
R2#clear ip route * –> use only when simulating something
R2#show ip route 104.0.0.0
% Network not in table
R2#show ip rip database 104.0.0.0 255.0.0.0
%Route not in database
R2 filters incoming update about net 104.0.0.0/8 from both Route-Server and R3, in other words it prevents route installation in its rip database regardless of the source of the incoming update.
——————- NOTE ———————–
The distribute-list is not a standalone filtering mechanism, the distribute-list command lets us to apply different filtering mechanisms to a routing process.
—————- END NOTE ——————-
I can be more specific when using a distribute-list and filtering only the update coming in from a specific neighbor–>link–>interface. For example let’s suppose that R2 must learn about network 104.0.0.0/8 only from R3 and not directly from the route-server, here what can I do using the same ACL defined before:
R2(config)#router rip
R2(config-router)#no distribute-list NET-104 in
R2(config-router)#do clear ip route *
R2#show ip route 104.0.0.0
Routing entry for 104.0.0.0/8
Known via “rip”, distance 120, metric 1
Redistributing via rip
Last update from 10.0.6.254 on FastEthernet0/1, 00:00:05 ago
Routing Descriptor Blocks:
* 10.0.6.254, from 10.0.6.254, 00:00:05 ago, via FastEthernet0/1
Route metric is 1, traffic share count is 1
R2 knows again about net 104.0.0.0/8.
R2(config)#router rip
R2(config-router)#distribute-list NET-104 in fastethernet 0/1
R2#show run | s r r
router rip
version 2
network 10.0.0.0
distribute-list NET-104 in FastEthernet0/1
I applied the same ACL only for routing update coming in from interface Fa0/1, so now R2 will reach net 104.0.0.0/8 in two hops via R3 on fa1/1
R2#show ip route 104.0.0.0
Routing entry for 104.0.0.0/8
Known via “rip”, distance 120, metric 2
Redistributing via rip
Last update from 10.0.2.3 on FastEthernet1/1, 00:00:05 ago
Routing Descriptor Blocks:
* 10.0.2.3, from 10.0.2.3, 00:00:05 ago, via FastEthernet1/1
Route metric is 2, traffic share count is 1
NOTE: You can find at this link a tricky effect caused by auto-summary, redistribution and filtering. Be careful when redistributing and filtering.
Let’s move forward with filtering techniques. I restore proper routing, letting R2 be able to receive update about all networks from Route-Server
R2(config)#router rip
R2(config-router)#no distribute-list NET-104 in F0/1
So far I tested distribute-list calling a standard ACL. the sintax for the ACL is:
permit/deny [ip-address] [wildcard-mask] – when called by a distribute list we can interpret it as:
permit/deny [network-address(prefix)] [wildcard-mask]
I have no possibility to match the MASK of the Route I’m trying to match. I remove for a moment auto-summary from rip process of Route-Server, R2 and R3 and I add a temporary /25 Loopback (ok loopback /25 doesn’t make too much sense but here I use it just for testing) on R3 with an ip address starting with 104.
R2(config)#router rip
R2(config-router)#no auto-summary
R3(config)#router rip
R3(config-router)#no auto-summary
Route-Server(config)#router rip
Route-Server(config-router)#no auto-summary
Now R2 receives three networks 104.x.x.x:
R2#show ip route 104.0.0.0
Routing entry for 104.0.0.0/8, 3 known subnets
Variably subnetted with 3 masks
Redistributing via rip
R 104.219.202.48/29 [120/1] via 10.0.6.254, 00:00:24, FastEthernet0/1
R 104.54.143.0/25 [120/1] via 10.0.2.3, 00:00:05, FastEthernet1/1
R 104.54.143.0/24 [120/1] via 10.0.6.254, 00:00:24, FastEthernet0/1
Suppose we want to filter only the newly created R3’s network –> 104.54.143.0/25. Can I do that with a distribute-list calling a standard ACL?
If I use the standard ACL used before:
R2#show run | s ip access
ip access-list standard NET-104
deny 104.0.0.0 0.255.255.255
permit any
R2#show ip route 104.0.0.0
Load for five secs: 8%/0%; one minute: 3%; five minutes: 5%
Time source is user configuration, 00:25:11.087 UTC Wed Aug 13 2014
Routing entry for 104.0.0.0/8, 3 known subnets
Variably subnetted with 3 masks
Redistributing via rip
R 104.219.202.48/29 [120/1] via 10.0.6.254, 00:02:25, FastEthernet0/1
R 104.54.143.0/25 [120/1] via 10.0.2.3, 00:02:47, FastEthernet1/1
R 104.54.143.0/24 [120/1] via 10.0.6.254, 00:02:25, FastEthernet0/1
After Hold-Down (180sec) Expires
R2#show ip route 104.0.0.0
Load for five secs: 1%/0%; one minute: 2%; five minutes: 5%
Time source is user configuration, 00:26:10.603 UTC Wed Aug 13 2014
Routing entry for 104.0.0.0/8, 3 known subnets
Variably subnetted with 3 masks
Redistributing via rip
R 104.219.202.48/29 is possibly down,
routing via 10.0.6.254, FastEthernet0/1
R 104.54.143.0/25 is possibly down,
routing via 10.0.2.3, FastEthernet1/1
R 104.54.143.0/24 is possibly down,
routing via 10.0.6.254, FastEthernet0/1
After the Flush Timer I see no 104.x.x.x so I filtered all net 104.x.x.x
R2#show ip route 104.0.0.0
Load for five secs: 1%/0%; one minute: 2%; five minutes: 4%
Time source is user configuration, 00:27:31.403 UTC Wed Aug 13 2014
% Network not in table
Ok, one might think –> I can play with a more specific wild card –> [104.54.143.0] [0.0.0.127] does it work?
R2#show run | s ip access
ip access-list standard NET-104
deny 104.54.143.0 0.0.0.127
permit any
R2#show ip route 104.0.0.0
Load for five secs: 3%/0%; one minute: 6%; five minutes: 5%
Time source is user configuration, 00:38:58.599 UTC Wed Aug 13 2014
Routing entry for 104.0.0.0/8, 3 known subnets
Variably subnetted with 3 masks
Redistributing via rip
R 104.219.202.48/29 [120/1] via 10.0.6.254, 00:00:22, FastEthernet0/1
R 104.54.143.0/25 is possibly down,
routing via 10.0.2.3, FastEthernet1/1
R 104.54.143.0/24 is possibly down,
routing via 10.0.6.254, FastEthernet0/1
R2#show ip route 104.0.0.0
Load for five secs: 1%/0%; one minute: 1%; five minutes: 2%
Time source is user configuration, 00:50:58.951 UTC Wed Aug 13 2014
Routing entry for 104.0.0.0/29, 1 known subnets
Redistributing via rip
R 104.219.202.48 [120/1] via 10.0.6.254, 00:00:22, FastEthernet0/1
Answer is NO. With wild-card 0.0.0.127 –> 0.0.0.01111111 I’m matching all network addresses with first 25 bit = 01101000.00110110.10001111.0 so I’m matching 104.54.143.0/24 too. The same would happen if I changed wild-card in 0.0.0.255, I will stil matching both the routes 104.54.143.0/[24,25].
The problem is that a distribute-list referencing a standard ACL cannot take into account the MASK portion of the ip prefix [network-address/mask-length] to match, so in cases where we have many prefixes with same network-address (net-add) portion and different mask-length (mask-len) we cannot use standard ACL referenced in a distribute-list, because we cannot distinguish among them.
What about using an Extended ACL (ext-ACl) instead?
$$$$$$$ EXTENDED ACCESS-LIST $$$$$$$
An extended ACL is:
permit/deny [protocol] [source address] [wildcard mask] eq [source-port] [destination address] [wildcard mask] eq [destination-port]
Here I want work with IP Routes/prefixes, so protocol is IP and I don’t need to worry about port number, so it reduces to:
permit/deny ip [source ip address] [wildcard mask] [destination ip address] [wildcard mask]
When applied to a Route-Filter IOS reads source and destination extended ACL fields in different ways, based upon what is referencing ext-ACL and which is the routing protocol in use:
CONDITION 1] distribute-list referencing ext-ACL and routing protocol is BGP, IOS reads source and destination fields in this way:
[source ip address][wildcard mask] = [NETWORK ADDRESS][wildcard mask] => match a specific portion of the configured ADDRESS based on wildcard
[destination ip address][wildcard mask] = [NETWORK MASK][wildcard mask] => match a specific portion of the configured MASK based on wildcard => Mask Length
Examples:
1a – permit ip 20.15.0.0 0.0.0.0 255.255.255.0 0.0.0.0 –> match network 20.15.0.0/24
1b – permit ip 20.15.0.0 0.0.255.255 255.255.255.0 0.0.0.0 –> match networks 20.15.x.x with mask length /24
1c – permit ip 20.15.0.0 0.0.255.255 255.255.255.128 0.0.0.127 –> match networks 20.15.x.x with mask length from /25(included) to /32(included)
1d – permit ip 20.15.0.0 255.255.255.255 0.0.0.0 255.255.255.255 –> match all networks + match all mask length = MATCH ALL
Here what rules the match result is the wildcard 0–>check | 1–>ignore
To test this I activate 2 BGP sessions Route-Server<->PE1, Route-Server<->PE2. Before doing that I stop connected redistribution into RIP at Route-Server and I clean all routing protocol configuration on R2 and R3 (no prefix-list, no route-map, no access-list on RIP). I set some Loopbacks on PE1 and PE2:
Codes: L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
C 1.0.0.254 is directly connected, Loopback1
C 10.0.1.0/24 is directly connected, Ethernet0/1
C 20.15.1.0/24 is directly connected, Loopback101
C 20.15.3.0/24 is directly connected, Loopback103
C 20.15.5.0/24 is directly connected, Loopback105
C 20.15.7.128/25 is directly connected, Loopback201
C 20.15.9.192/26 is directly connected, Loopback203
C 20.15.11.254/32 is directly connected, Loopback205
PE2#show ip route conn | i C
Codes: L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
C 2.0.0.254 is directly connected, Loopback2
C 10.0.5.0/24 is directly connected, Ethernet0/0
C 20.15.0.0/24 is directly connected, Loopback100
C 20.15.2.0/24 is directly connected, Loopback102
C 20.15.4.0/24 is directly connected, Loopback104
C 20.15.6.224/27 is directly connected, Loopback200
C 20.15.8.240/28 is directly connected, Loopback202
C 20.15.10.248/29 is directly connected, Loopback204
After establishing BGP sessions and injecting the network into BGP at PE1 and PE2, on Route-Server I see all the routes 20.x.x.x:
Route-Server#show ip route bgp | b 20.
20.0.0.0/8 is variably subnetted, 12 subnets, 7 masks
B 20.15.0.0/24 [200/0] via 2.0.0.254, 00:01:37
B 20.15.1.0/24 [200/0] via 1.0.0.254, 00:02:40
B 20.15.2.0/24 [200/0] via 2.0.0.254, 00:01:34
B 20.15.3.0/24 [200/0] via 1.0.0.254, 00:02:40
B 20.15.4.0/24 [200/0] via 2.0.0.254, 00:01:31
B 20.15.5.0/24 [200/0] via 1.0.0.254, 00:02:40
B 20.15.6.224/27 [200/0] via 2.0.0.254, 00:01:17
B 20.15.7.128/25 [200/0] via 1.0.0.254, 00:02:40
B 20.15.8.240/28 [200/0] via 2.0.0.254, 00:00:41
B 20.15.9.192/26 [200/0] via 1.0.0.254, 00:02:40
B 20.15.10.248/29 [200/0] via 2.0.0.254, 00:00:26
B 20.15.11.254/32 [200/0] via 1.0.0.254, 00:02:40
Now suppose we want to use a distribute-list calling an ext-ACl to do some BGP filtering:
NOTE: It’s better configuring the distribute-list per neighbor because with both 15.4(S5) and 15.41T I see odd behaviour when using only distribute-list in.
a) permit only 20.15.0.0/24
Route-Server(config)#ip access-list extended 100
Route-Server(config-ext-nacl)#5 permit ip 20.15.0.0 0.0.0.0 255.255.255.0 0.0.0.0
Route-Server#show ip access-lists
Extended IP access list 100
5 permit ip host 20.15.0.0 host 255.255.255.0
Route-Server(config)#router bgp 1000
Route-Server(config-router)#address-family ipv4 unicast
Route-Server(config-router-af)#neighbor 1.0.0.254 distribute-list 100 in
Route-Server(config-router-af)#neighbor 2.0.0.254 distribute-list 100 in
router bgp 1000
bgp router-id 14.14.14.14
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 1.0.0.254 remote-as 1000
neighbor 1.0.0.254 update-source Loopback14
neighbor 2.0.0.254 remote-as 1000
neighbor 2.0.0.254 update-source Loopback14
!
address-family ipv4
neighbor 1.0.0.254 activate
neighbor 1.0.0.254 next-hop-self
neighbor 1.0.0.254 distribute-list 100 in
neighbor 2.0.0.254 activate
neighbor 2.0.0.254 next-hop-self
neighbor 2.0.0.254 distribute-list 100 in
PE1#clear ip bgp ipv4 unicast 1000 soft out
PE2#clear ip bgp ipv4 unicast 1000 soft out
Route-Server#show ip route bgp | b 20.
20.0.0.0/24 is subnetted, 1 subnets
B 20.15.0.0 [200/0] via 2.0.0.254, 00:11:43
b) permit networks 20.15.x.x with mask length /24
Route-Server(config)#no ip access-list extended 100
Route-Server(config)#ip access-list extended 100
Route-Server(config-ext-nacl)#5 permit ip 20.15.0.0 0.0.255.255 255.255.255.0 0.0.0.0
Route-Server#show ip access-lists 100
Extended IP access list 100
5 permit ip 20.15.0.0 0.0.255.255 host 255.255.255.0 (6 matches)
PE1#clear ip bgp ipv4 unicast 1000 soft out
PE2#clear ip bgp ipv4 unicast 1000 soft out
Route-Server#show ip route bgp | b 20.
20.0.0.0/24 is subnetted, 6 subnets
B 20.15.0.0 [200/0] via 2.0.0.254, 00:07:56
B 20.15.1.0 [200/0] via 1.0.0.254, 00:07:55
B 20.15.2.0 [200/0] via 2.0.0.254, 00:07:56
B 20.15.3.0 [200/0] via 1.0.0.254, 00:07:55
B 20.15.4.0 [200/0] via 2.0.0.254, 00:07:56
B 20.15.5.0 [200/0] via 1.0.0.254, 00:07:55
c) permit networks 20.15.x.x with mask length from /25(included) to /32(included)
Route-Server(config)#no access-list 100
Route-Server(config)#access-list 100 permit ip 20.15.0.0 0.0.255.255 255.255.255.128 0.0.0.127
Route-Server#show run | s access-list
access-list 100 permit ip 20.15.0.0 0.0.255.255 255.255.255.128 0.0.0.127
Route-Server#show access-lists
Extended IP access list 100
10 permit ip 20.15.0.0 0.0.255.255 255.255.255.128 0.0.0.127 (6 matches)
Route-Server#show ip route bgp | b 20.
20.0.0.0/8 is variably subnetted, 6 subnets, 6 masks
B 20.15.6.224/27 [200/0] via 2.0.0.254, 00:06:24
B 20.15.7.128/25 [200/0] via 1.0.0.254, 00:06:24
B 20.15.8.240/28 [200/0] via 2.0.0.254, 00:06:24
B 20.15.9.192/26 [200/0] via 1.0.0.254, 00:06:24
B 20.15.10.248/29 [200/0] via 2.0.0.254, 00:06:24
B 20.15.11.254/32 [200/0] via 1.0.0.254, 00:06:24
d) deny networks 20.15.x.x with mask length /24 and 20.15.x.x with mask length from /27 to /32
Route-Server(config)#no access-list 100
Route-Server(config)#access-list 100 deny ip 20.15.0.0 0.0.255.255 255.255.255.0 0.0.0.0
Route-Server(config)#access-list 100 deny ip 20.15.0.0 0.0.255.255 255.255.255.224 0.0.0.31
Route-Server(config)#access-list 100 permit ip any any
Route-Server#show ip access-lists
Extended IP access list 100
10 deny ip 20.15.0.0 0.0.255.255 host 255.255.255.0
20 deny ip 20.15.0.0 0.0.255.255 255.255.255.224 0.0.0.31
30 permit ip any any
Route-Server#show ip bgp | b Net
Network Next Hop Metric LocPrf Weight Path
*>i 20.15.7.128/25 1.0.0.254 0 100 0 i
*>i 20.15.9.192/26 1.0.0.254 0 100 0 i
Route-Server#show ip route bgp | b 20.
20.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
B 20.15.7.128/25 [200/0] via 1.0.0.254, 00:23:28
B 20.15.9.192/26 [200/0] via 1.0.0.254, 00:23:28
e) deny all
Route-Server(config)#no access-list 100
Route-Server(config)#access-list 100 deny ip 1.2.3.4 255.255.255.255 5.6.7.8 255.255.255.255
Route-Server#show access-lists
Extended IP access list 100
10 deny ip any any
Route-Server#show ip bgp | b Net –> No path into BGP table
Route-Server#show ip route bgp | b 20. –> No route BGP in routing table
NOTE: General Rule –> If distribute-list is referencing a non-existent ACL nothing happens
————– NOTE —————–
Route-Server(config)#ip access-list extended TEST-NAMED
Route-Server(config-ext-nacl)#5 permit ip any any
Route-Server(config)#router bgp 1000
Route-Server(config-router)#address-family ipv4 unicast
Route-Server(config-router-af)#distribute-list TEST-NAMED in
% The ACL cannot be created or an ACL with the same name but incompatible type already exists –> this with code 15.x
Access-list type conflicts with prior definition – % This command only accepts named standard IP access-lists –> this with code 12.x
EXTENDED NAMED ACL instead seems to be supported per neighbor in BGP
Route-Server(config-router-af)#neighbor 1.0.0.254 distribute-list TEST-NAMED in
———— END NOTE —————-
CONDITION 2] the same logic of CONDITION-1] is applied when using an Extended ACL referenced by a route-map when filtering during a redistribution. Here again the logic:
[source ip address][wildcard mask]= [NETWORK ADDRESS][wildcard mask] => match a specific portion of the configured ADDRESS based on wildcard
[destination ip address][wildcard mask] = [NETWORK MASK][wildcard mask] => match a specific portion of the configured MASK based on wildcard => Mask Length
The important difference with CONDITION-1] is that the logic is valid for route-map when filtering during a redistribution for BOTH IGP and BGP protocols and not only for BGP
Example:
– Suppose that now we want inject some of the connected Loopbacks of Route-Server in the RIP domain for example these two subnet of net 104.x.x.x
Route-Server#show ip route 104.0.0.0 | i C
C 104.54.143.0/24 is directly connected, Loopback10100
C 104.219.202.48/29 is directly connected, Loopback10053
I can do that redistributing connected interfaces filtered by a route-map calling an Extended-ACL.
Route-Server(config)#ip access-list extended NET-104
Route-Server(config-ext-nacl)#5 permit ip 104.54.143.0 0.0.0.0 255.255.255.0 0.0.0.0
Route-Server(config-ext-nacl)#10 permit ip 104.219.202.48 0.0.0.0 255.255.255.248 0.0.0.0
Route-Server#show run | s route-map
route-map 104-INTO-RIP permit 10
match ip address NET-104
Route-Server(config)#router rip
Route-Server(config-router)#redistribute connected route-map 104-INTO-RIP
Route-Server#show ip access-lists
Extended IP access list NET-104
5 permit ip host 104.54.143.0 host 255.255.255.0 (1 match)
10 permit ip host 104.219.202.48 host 255.255.255.248 (1 match)
I see the two routes in rip database:
Route-Server#show ip rip database | b 104
104.0.0.0/8 auto-summary
104.54.143.0/24 redistributed
[1] via 0.0.0.0,
104.219.202.48/29 redistributed
[1] via 0.0.0.0,
and received for example by R2:
R2#show ip route rip
1.0.0.0/32 is subnetted, 1 subnets
R 1.0.0.254 [120/2] via 10.0.2.3, 00:00:01, FastEthernet1/1
2.0.0.0/32 is subnetted, 1 subnets
R 2.0.0.254 [120/1] via 10.0.5.254, 00:00:08, FastEthernet0/0
10.0.0.0/24 is subnetted, 9 subnets
R 10.0.3.0 [120/1] via 10.0.2.3, 00:00:01, FastEthernet1/1
R 10.0.0.0 [120/1] via 10.0.6.254, 00:00:24, FastEthernet0/1
[120/1] via 10.0.2.3, 00:00:01, FastEthernet1/1
R 10.0.1.0 [120/1] via 10.0.2.3, 00:00:01, FastEthernet1/1
R 10.0.4.0 [120/1] via 10.0.2.3, 00:00:01, FastEthernet1/1
104.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
R 104.219.202.48/29 [120/1] via 10.0.6.254, 00:00:24, FastEthernet0/1
R 104.54.143.0/24 [120/1] via 10.0.6.254, 00:00:24, FastEthernet0/1
14.0.0.0/32 is subnetted, 1 subnets
R 14.14.14.14 [120/1] via 10.0.6.254, 00:00:24, FastEthernet0/1
so route-map and ext-ACL are working as expected for RIP. The same logic works with BGP using route-map referencing an Ext-ACL. As an Example for BGP suppose that I want redistribute into BGP another pair of connected Loopbacks of Route-Server:
Route-Server#show ip route 85.0.0.0 | i C
C 85.95.192.0/19 is directly connected, Loopback10039
C 85.140.0.0/17 is directly connected, Loopback10069
Route-Server(config)#ip access-list extended NET-85
Route-Server(config-ext-nacl)#5 permit ip 85.95.192.0 0.0.0.0 255.255.224.0 0.0.0.0
Route-Server(config-ext-nacl)#10 permit ip 85.140.0.0 0.0.0.0 255.255.128.0 0.0.0.0
Route-Server(config)#route-map 85-INTO-BGP permit 10
Route-Server(config-route-map)#match ip address NET-85
Route-Server(config)#router bgp 1000
Route-Server(config-router)#address-family ipv4 unicast
Route-Server(config-router-af)#redistribute connected route-map 85-INTO-BGP
Route-Server#show ip access-lists
Extended IP access list NET-85
5 permit ip host 85.95.192.0 host 255.255.224.0 (2 matches)
10 permit ip host 85.140.0.0 host 255.255.128.0 (2 matches)
Routes are correctly injected into BGP table
Route-Server#show ip bgp | b 85.
*> 85.95.192.0/19 0.0.0.0 0 32768 ?
*> 85.140.0.0/17 0.0.0.0 0 32768 ?
and received by BGP neighbors:
PE1#show ip route 85.0.0.0
Routing entry for 85.0.0.0/8, 2 known subnets
Variably subnetted with 2 masks
B 85.95.192.0/19 [200/0] via 14.14.14.14, 00:03:07
B 85.140.0.0/17 [200/0] via 14.14.14.14, 00:03:07
PE2#show ip route 85.0.0.0
Routing entry for 85.0.0.0/8, 2 known subnets
Variably subnetted with 2 masks
B 85.95.192.0/19 [200/0] via 14.14.14.14, 00:03:38
B 85.140.0.0/17 [200/0] via 14.14.14.14, 00:03:38
This shows that Ext-ACL can be referenced by a route-map for redistributing/filtering purpose and that the logic
[source ip address][wildcard mask] = [NETWORK ADDRESS][wildcard mask] => match a specific portion of the configured ADDRESS based on wildcard
[destination ip address][wildcard mask] = [NETWORK MASK][wildcard mask] => match a specific portion of the configured MASK based on wildcard => Mask Length
is valid both for BGP and IGP (tested RIP).
————– NOTE ——————
To remember when using route-map calling an ACL (standard or extended and the same concept is true when calling a prefix-list) is that the permit/deny rules of the ACLs (prefix-list) never determine if the route is permitted/discarded but ALWAYS are the permit/deny action defined in route-map statements that decide if a route is permitted/denied. The permit/deny rules of ACLs (prefix-list) when invoked by a route-map only influences if the set of routes must be considered (if rule is permit) or must not be considered (if rule is deny) against a single route-map statement action (permit/deny). You can find more details here
———— END NOTE —————-
CONDITION-3] distribute-list referencing ext-ACL and routing protocol is an IGP (RIP,OSFP,EIGRP) IOS reads source and destination fields in this way:
[source ip address][wildcard mask] = [ROUTE’S GATEWAY IP ADDRESS][wildcard mask] => match the ip address of the device to exit toward the route.
[destination ip address][wildcard mask] = [NETWORK ADDRESS][wildcard mask] => match the network portion of the ip prefix.
From the above description we can see that in this case the interpretation of ext-ACL fields are very different, we can match the ip address by which we received update about the route we want to filter (gateway of the route) and the network portion of the ip prefix, again even if we are using an Extended-ACL we cannot match the mask length.
This filtering tool can be useful when we receive the same network information from two different sources. It’s a very specific case but as an example I can consider this one:
R2 is receiving via rip network 10.0.0.0/24 from both R3 and Route-Server (is the link connecting R3 to Route-Server).
R2#show ip route rip
1.0.0.0/32 is subnetted, 1 subnets
R 1.0.0.254 [120/2] via 10.0.2.3, 00:00:13, FastEthernet1/1
2.0.0.0/32 is subnetted, 1 subnets
R 2.0.0.254 [120/1] via 10.0.5.254, 00:00:07, FastEthernet0/0
10.0.0.0/24 is subnetted, 9 subnets
R 10.0.3.0 [120/1] via 10.0.2.3, 00:00:13, FastEthernet1/1
R 10.0.0.0 [120/1] via 10.0.6.254, 00:00:14, FastEthernet0/1
[120/1] via 10.0.2.3, 00:00:13, FastEthernet1/1
R 10.0.1.0 [120/1] via 10.0.2.3, 00:00:13, FastEthernet1/1
R 10.0.4.0 [120/1] via 10.0.2.3, 00:00:13, FastEthernet1/1
104.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
R 104.219.202.48/29 [120/1] via 10.0.6.254, 00:00:14, FastEthernet0/1
R 104.54.143.0/24 [120/1] via 10.0.6.254, 00:00:14, FastEthernet0/1
14.0.0.0/32 is subnetted, 1 subnets
R 14.14.14.14 [120/1] via 10.0.6.254, 00:00:14, FastEthernet0/1
This is the only one network of type 10.x.x.x received via Route-Server. Suppose we don’t want to receive update via rip about this network from Route-Server, I can apply an ext-ACL invoked by a distribute-list in this way:
R2(config)#ip access-list extended 100
R2(config-ext-nacl)#5 deny ip 10.0.6.254 0.0.0.0 10.0.0.0 0.0.0.0 –> match gateway 10.0.6.254 network 10.0.0.0
R2(config-ext-nacl)#10 permit ip any any
R2#show ip route rip
Load for five secs: 0%/0%; one minute: 2%; five minutes: 1%
Time source is user configuration, 22:26:30.871 UTC Wed Aug 13 2014
…………………
10.0.0.0/24 is subnetted, 9 subnets
R 10.0.3.0 [120/1] via 10.0.2.3, 00:00:09, FastEthernet1/1
R 10.0.0.0 [120/1] via 10.0.6.254, 00:02:23, FastEthernet0/1
[120/1] via 10.0.2.3, 00:00:09, FastEthernet1/1
R 10.0.1.0 [120/1] via 10.0.2.3, 00:00:09, FastEthernet1/1
R 10.0.4.0 [120/1] via 10.0.2.3, 00:00:09, FastEthernet1/1
…………………
R2#show ip route rip
Load for five secs: 0%/0%; one minute: 2%; five minutes: 1%
Time source is user configuration, 22:26:42.723 UTC Wed Aug 13 2014
…………………
10.0.0.0/24 is subnetted, 9 subnets
R 10.0.3.0 [120/1] via 10.0.2.3, 00:00:21, FastEthernet1/1
R 10.0.0.0 [120/1] via 10.0.6.254, 00:02:35, FastEthernet0/1
[120/1] via 10.0.2.3, 00:00:21, FastEthernet1/1
R 10.0.1.0 [120/1] via 10.0.2.3, 00:00:21, FastEthernet1/1
R 10.0.4.0 [120/1] via 10.0.2.3, 00:00:21, FastEthernet1/1
…………………
We can see that entry for 10.0.0.0/24 is going in holdown (I don’t see the periodic refresh of the route every 30 sec). After flush timer expires the route is gone.
R2#show ip route 10.0.0.0 255.255.255.0
Load for five secs: 1%/0%; one minute: 1%; five minutes: 1%
Time source is user configuration, 22:29:00.751 UTC Wed Aug 13 2014
Routing entry for 10.0.0.0/24
Known via “rip”, distance 120, metric 1
Redistributing via rip
Last update from 10.0.2.3 on FastEthernet1/1, 00:00:34 ago
Routing Descriptor Blocks:
* 10.0.2.3, from 10.0.2.3, 00:00:24 ago, via FastEthernet1/1
Route metric is 1, traffic share count is 1
With distribute-list_ext-ACL we cannot filter same network prefixes with different mask lenght from the same source.
$$$$$$$ PREFIX-LIST $$$$$$$
As we saw we can reference ACLs (standard/extended) inside a route-filter, but the core function of an ACL is to block specific packets, in other words ACL is a more general tool not specific to route-filtering. Prefix-List instead are a tool born specifically to filter routes. Simply speaking a prefix-list is similar to an ACL but is more flexible in managing subnet mask and set of routes.
A prefix-list can be written in this way:
ip prefix-list (NAME) [seq-num1] [permit/deny] [ip-prefix] ge [Minimum prefix length to be matched] le [Maximum prefix length to be matched]
ip prefix-list (NAME) [seq-num2] [permit/deny] [ip-prefix] ge [Minimum prefix length to be matched] le [Maximum prefix length to be matched]
ip prefix-list (NAME) [seq-num3] [permit/deny] [ip-prefix] ge [Minimum prefix length to be matched] le [Maximum prefix length to be matched]
[ip-prefix = [network-address]/[mask-length]
So it’s an ordered (based on ) list of permit/deny rules directly applied to ip prefix. Here we don’t need to worry about wildcard calculation to define the mask length, we can simply write /8 /21 /12 and so on. What give us much more flexibility than an ACL are the ge (greater equal)/le (lesser equal) options at the end of the command. With these options I can define a range of mask length to be matched.
Before going on with another test I clean configuration about redistribution and filtering on Route-Server, then let’s suppose to control redistribution and filtering with prefix-list.
As first step I want redistribute into rip not all the connected loopbacks of Route-Server but only a subset containing network belonging to this address space [0.x.x.x – 31.x.x.x]/mask-len >= 8 – to filter unwanted routes I will use a route-map named SELECTOR calling a prefix-list.
If I used an extended ACL configuration could be:
ip access-list extended INJECTOR
permit ip 0.0.0.0 31.255.255.255 255.0.0.0 0.255.255.255
route-map SELECTOR permit 10
match ip address INJECTOR
Routes-Server(config)#router rip
Routes-Server(config-router)#redistribute connected route-map SELECTOR
Using a prefix-list becomes:
Routes-Server(config)#ip prefix-list INJECTOR permit 0.0.0.0/3 ge 8 –> match all network address with first 3 bits = 000 (0 -> 31) and with 8 <= mask-length <= 32.
Let’s try:
Route-Server(config)#ip prefix-list INJECTOR permit 0.0.0.0/3 ge 8
Route-Server(config)#route-map SELECTOR permit 10
Route-Server(config-route-map)#match ip address prefix-list INJECTOR
Route-Server(config)#router rip
Route-Server(config-router)#redistribute connected route-map SELECTOR
In rip database of Route-Server I see only routes (0.x.x.x – 31.x.x.x)/8(+) permitted by the route-map as expected (and networks 10.0.0.0/24, 10.0.6.0/24, 14.14.14.14/32 connected interfaces of Route-Server covered by network command under RIP and this is expected too) – more details about that and about the relation between permit/deny rules of an ACL/prefix-list with permit/deny action of a route-map can be found here
————— NOTE —————-
The prefix-list INJECTOR works because I decided to take networks with mask-length >= 8 for the address space (0.x.x.x – 31.x.x.x), but if for example I had to redistribute also networks in the same address space (0.x.x.x – 31.x.x.x) but with shorter mask-length too, the best I could do will be:
permit 0.0.0.0/3 le 32 –> match all network address with first three bits = 000 and with 3 <= mask-length <= 32, so with a single entry not all possible mask length can be matched, for example all network in range (0.x.x.x – 31.x.x.x) with mask-length <= 2 will not match. In such case an extended-ACL would be more efficient:
ip access-list extended INJECTOR
permit ip 0.0.0.0 31.255.255.255 0.0.0.0 255.255.255.255
————- END NOTE ————–
What rules a prefix-list is a set of four pieces:
ip prefix-list (NAME) [permit/deny] [seq-num] [net-add]/[cfg-len] ge [min-len] le [max-len]
1] configured network address [net-add]
2] configured length mask [cfg-len]
3] ge [min-len]
4] le [max-len]
Then we must respect –> cfg-len < min-len <= max-len <= 32
The logic then changes if ge/le are present or not.
If ge/le are not used –> cfg-len defines the EXACT MASK LENGHT and net-add must be an EXACT MATCH. For example:
permit 10.0.0.0/8 means –> network 10.0.0.0 with mask /8
permit 10.1.1.0/8 means –> network 10.1.1.0 with mask /8
If only ge is present –> cfg-len < min-len <= 32 –> cgf-len defines how many bits of net-add must be checked and length of network to be matched must be included in this interval [min-len (included), 32]. For Example:
permit 10.0.0.0/7 ge 8 –> check first 7 bits of net-add => 0000101|0 – ge 8 => mask can be in length from 8 to 32
Here I’m matching among many others –> 10.0.0.0/8 10.0.0.0/9 10.1.0.0/16 10.3.0.0/24 but 11.0.0.0/8 11.1.0.0/29 11.11.11.11/32 too
If only le is present –> cfg-len <= max-len <= 32 –> cfg-len defines how many bits of net-add must be checked and length of network to be matched must be included in this interval [cfg-len (included), max-len(included)]
permit 10.1.0.0/16 le 24 –> networks must start with 10.1 and mask can be from 16 (inlcuded) to 24 (included)
If ge and le are present –> cfg-len < min-len <= max-len <= 32 –> cfg-len defines how many bits of net-add must be checked and length of network to be matched must be included in this interval [min-len (included), max-len (included)]. For example:
permit 10.0.0.0/8 ge 9 le 29 –> networks must start with 10 in first octet and mask length can be included in [9(included),29(included]
Here I’m not matching for example network 10.0.0.0/8 because mask length (8) is not >= 9 , but I’m matching 10.0.0.0/9…10.0.0.0/24. If I had to include 10.0.0.0/8 I must add a statement –> permit 10.0.0.0/8 an Exact Match.
NOTE: The logic behind prefix-list can be tricky.
————– NOTE ——————
To remember when using route-map calling a prefix-list (and the same concept is true when calling an ACL too) is that the permit/deny rules of the prefix-list (ACL) never determine if the route is permitted/discarded but ALWAYS are the permit/deny action defined in route-map statements that decide if a route is permitted/denied. The permit/deny rules of a prefix-list (ACL) when invoked by a route-map only influences if the set of routes must be considered (if rule is permit) or must not be considered (if rule is deny) against a single route-map statement action (permit/deny). You can find more details here
———— END NOTE —————-
Last test I want do is calling an ip prefix-list with a distribute-list. Suppose we want receive at R4 and R5 only first half of the network space injected into rip by Route-Server (0.x.x.x – 31.x.x.x), I can do:
R2(config)#ip prefix-list NET-0-TO-15 seq 5 permit 0.0.0.0/4 le 32 –> match first 4 bits (0000) –> possible networks (0-15).x.x.x with 4<= mask-len <= 32
R2(config)#router rip
R2(config-router)#distribute-list prefix NET-0-TO-15 out fa1/12
R2(config-router)#distribute-list prefix NET-0-TO-15 out fa1/13
doing the same on R3 I get no subnets for networks >= 15.x.x.x so prefix-list is working.
R4#show ip route rip | ex 10.0
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
2.0.0.0/8 is variably subnetted, 3 subnets, 3 masks
4.0.0.0/8 is variably subnetted, 3 subnets, 3 masks
11.0.0.0/8 is variably subnetted, 3 subnets, 3 masks
12.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
13.0.0.0/8 is variably subnetted, 3 subnets, 3 masks
14.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
R5#show ip route rip | ex 10.0
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
2.0.0.0/8 is variably subnetted, 3 subnets, 3 masks
4.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
11.0.0.0/8 is variably subnetted, 3 subnets, 3 masks
12.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
13.0.0.0/8 is variably subnetted, 3 subnets, 3 masks
14.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
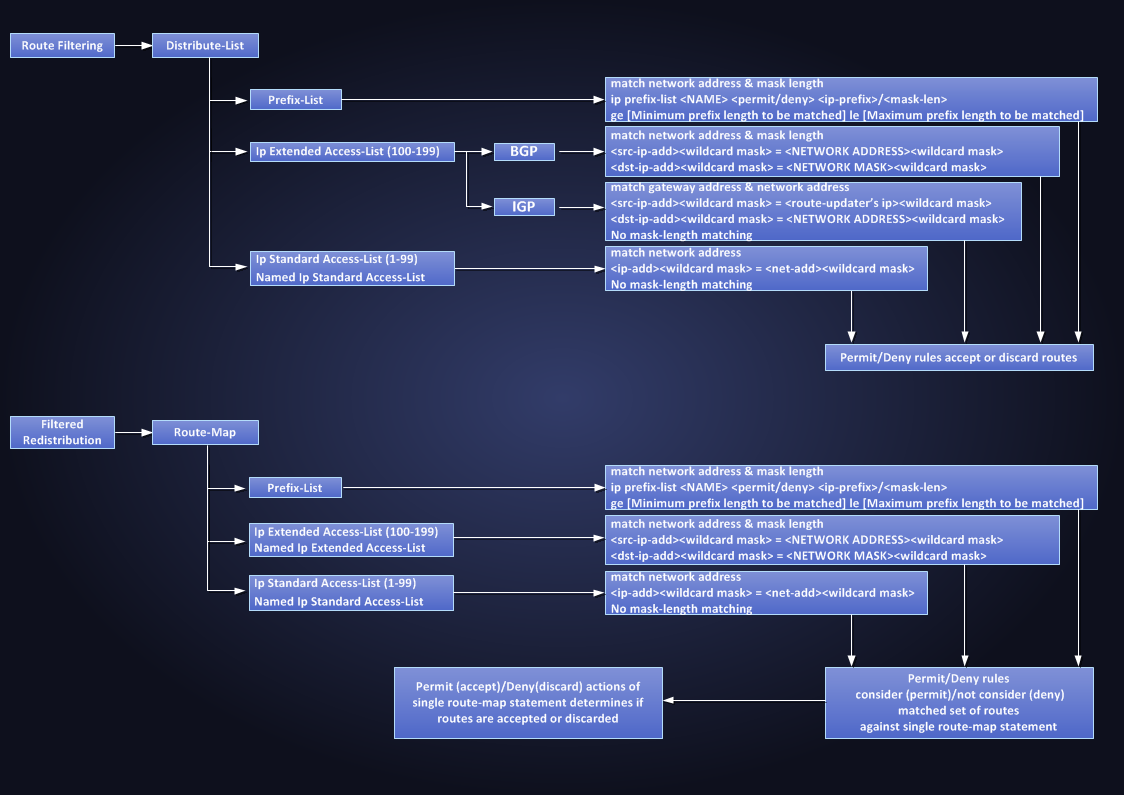
Now that I have a basic understanding of ACL (standard/extended) – Prefix-List – distribute-list and route-map used to filter routes, I’ll take each routing protocol and I’ll review all filtering methods specific to that protocol (wait for coming soon next arcticles…) Here a picture summarizing what I learned so far.